Share this article
In his role as Senior Security Engineer, Luis Phillip Tejido has been focused on enhancing the security service offerings at iQ3 (now Thales Cyber Services ANZ), including Managed Cyber Security, Vulnerability Management, Penetration Testing and Security Awareness. Luis started his career as a Linux/Unix System Administrator, who always had an interest in defensive and offensive cybersecurity. After his role as a system administrator, Luis decided to follow his passion, working at as a Security Engineer with a focus on targeting cybercriminals in order to protect organisations and individuals.
A Closer look the security risks of Remote Desktop Protocol (RDP) over the internet
What is RDP?
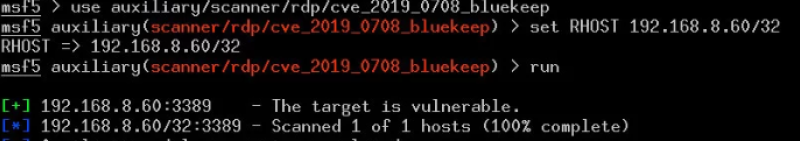
Remote Desktop is a remote management tool you can use with Windows that allows you to connect to any computer running Windows and take over the desktop, literally as if you were sitting in front of the monitor. Same idea as Teamviewer, Citrix GoToMyPC, LogMeIn, or any number of VNC clients and the good thing about this is its bundled with Windows. Nowadays its very common for businesses to use RDP as a method of access to servers to collaborate and access to files. For its wide range of functionality this has been a good target for cyber criminals. A recent report from Coverware has highlighted that RDP is the most dominant attack vector, being used 63.5% of disclosed targeted ransomware campaigns in Q1 2019. In addition to this the discovery of “BlueKeep” in this year 2019 that impacted Microsoft’s Remote Desktop Protocol (RDP). Despite of Microsoft’s effort releasing security updates, the vulnerability was widely exploited by Cyber Criminals.
Threats against RDP
- RDP can act as gateway for a cyber-criminal for an organization if not properly configured. This means they can have access to sensitive materials
- Cyber criminals can perform remote code execution that can take over the entire machine.
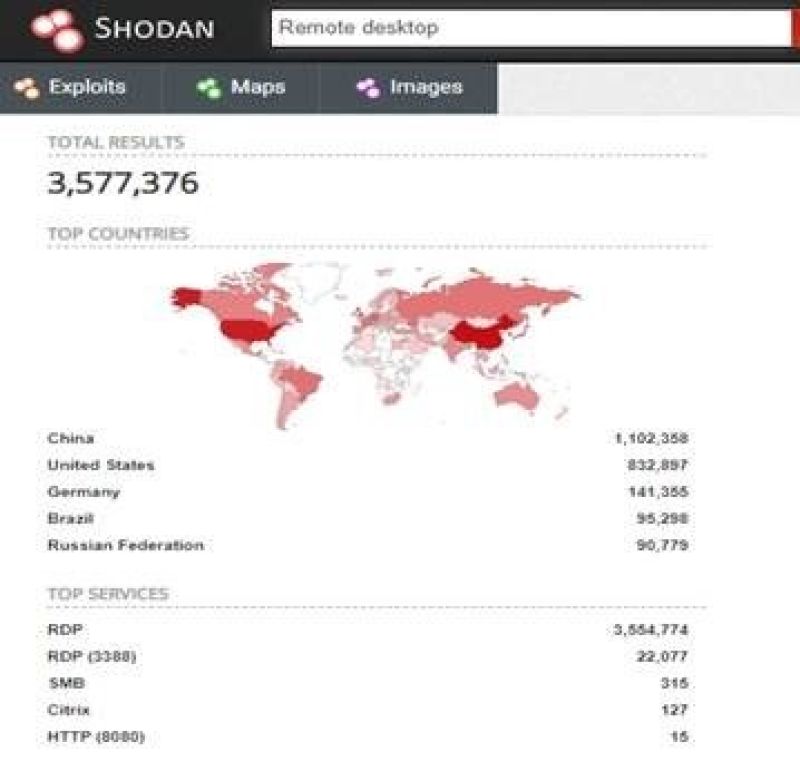
- Attackers has crafted a tool that continuously search for an organization or a single user that use RDP. Below is the simplest way of doing this search. A site called “Shodan” has the capability perform this kind of search:
Actions to be taken
- If you haven’t updated the software on your personal computer in a while. Microsoft says that vulnerable in-support systems (those still supported by the company) include Windows 7, Windows Server 2008 R2, and Windows Server 2008. Out-of-support systems include Windows 2003 and Windows XP. Customers running Windows 8 and Windows 10 are not affected by the vulnerability.
- Use firewalls to limit access. By default, it runs in port 3389 using an RDP gateway is also highly recommended for restricting RDP access to desktops and servers.
- Using strong passwords on any account with access to Remote Desktop is one of the top things to consider before enabling RDP.
- To prevent escalation privileges attack. Limit the remote access to those accounts that has administrator privilege.
For more information around cyber security and steps to ensure your organisation is protected, reach out to our team.
Contact us
Speak with a Thales Cyber Services ANZ
Security Specialist
Thales Cyber Services ANZ is a full-service cybersecurity and secure cloud services provider, partnering with clients from all industries and all levels of government. Let’s talk.




