Adversary Simulation
Adversary testing simulates an attack, testing your team’s capacity to detect, respond to an attack and to learn and improve.

Adversary testing simulates an attack, testing your team’s capacity to detect, respond to an attack and to learn and improve.
How we can assist:
What is an Adversary Simulation?
Why Adversary Simulation Services Matter to Your Organisation?
Understanding how threat actors operate is critical to building an effective cybersecurity strategy that protects your organisation from myriad risks. A policy that doesn’t consider how malicious actors ply their trade and where your specific vulnerabilities lie is unlikely to protect you from criminals intent on stealing your data, wreaking havoc with your systems and damaging your reputation.
Adversary simulation services assess your organisation’s true capacity to respond to an event by carrying out a detailed assessment of your threat surface and then testing your defensive capability through simulated attack scenarios.
A variety of different tools and tactics are used in adversary services. Using current understanding into what tactics, techniques, and procedures (TTPs) are performed by known threat actors, monitoring activity on the dark web and conducting a thorough analysis of your environment to understand how an attacker could breach your defences.
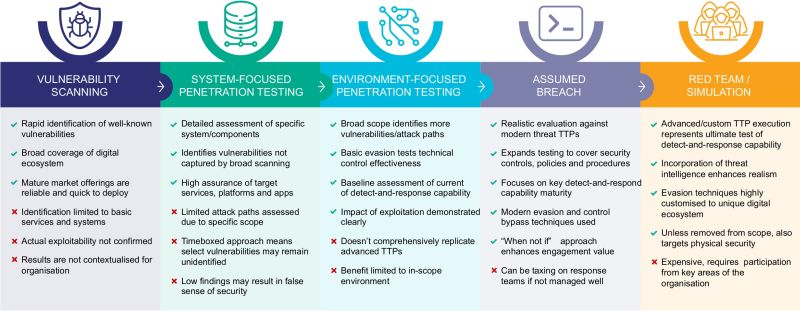
Organisations face a variety of different threats from a broad spectrum of different attackers. Understanding which threats relate to your organisation, which should be actively defended against, which should be monitored by technical assurance & testing services and which risks aren’t relevant is challenging in an ever-changing threat landscape.
Having the requisite skills and tools to detect, protect and respond to the cyber-criminals requires an understanding of where an attacker is likely to strike, how to block that attack and how to respond should a malicious actor gain a foothold in your systems.
Adversary simulation services include a number of different techniques including red teams who carry out reconnaissance and attempt to break into your systems, purple teams who build and test plans to block attackers, and external threat assessments that assist your organisation to uncover exposed and forgotten assets. Using the intelligence and knowledge from these teams allows your organisation to better understand the risks it faces and create mitigation plans to ensure your critical information and system assets are as well protected as possible.
Red Teaming comes in many flavours but relies on the fundamental premise: the replication/simulation of tactics, techniques, and procedures (TTPs) performed by known threat actors.
A Thales Cyber Services ANZ Red Teaming Engagement is a complex, comprehensive and multi-layered attack simulation on an organisation.
A Red team uses a custom set of tactics, techniques and procedures (TTPs) to assess your organisation's cyber resiliency against real-world adversaries. The Red Team assessment starts with the alignment/definition of objectives/goals and rules of the engagement, then defines the test plan and finally execution of the plan.
By mimicking a real cyber-attack, the output of your Thales Cyber Services ANZ Red Team engagement will provide your organisation with a detailed snapshot of the current level of your cyber resilience, covering your people, processes, and your technology. The report will guide you on how to prioritise improvements to your detection and response capabilities helping your company stay ahead of the adversaries.
Red Team exercises focus on all the vectors that real adversaries would. To simulate a real-world scenario, only key stakeholders are made aware of the exercise.
Purple Teaming uses intelligence gathered on threat actors to build a test plan to replicate the tactics, techniques and procedures (TTPs) that are most likely trying to breach your organisation's cybersecurity posture, usually targeting people, processes and technology but not limited to it.
Purple Team engagements merge the Red Team and Blue Team to simulate TTPs from known threat actors to implement or improve your organisation's cybersecurity posture. Usually, when doing a Purple Team exercise, the parts involved in the simulation select the threat actor based on information provided by Threat Intelligence teams. This is intended to tailor the defensive teams regarding threats targeting your organisation's industry and other demographics.
As an outcome, a Purple Team engagement is the best tool to check the detection and response in place, as well as to identify blind spots and solve them at execution/testing time.
Click to learn more about purple teaming
Testing your response plan and your crisis management skills is a vital step in ensuring a successful response to an incident. A Gold Teaming exercise provides a safe environment to test your policies, plans and procedures and hone your response skills before they’re needed.
We’ll collaborate with your team to develop a credible scenario that will involve, not just your IT team, but all facets of the business typically involved in a crisis response.
A tabletop exercise / Gold Team engagement is a discussion-based exercise that is aimed at testing and validating the current incident response plan and playbooks of an organisation. A facilitator will drive the discussion by presenting a scenario and various injections based on the scenario created. The scenario is typically customised according to the target organisation’s technology stack and is based on the most current threat intelligence.
The following parts of the business are recommended to be involved in a Gold Team engagement:
Potential scenarios include testing your response to a:
At the end of a Thales Cyber Services ANZ Gold Teaming engagement, you’ll know what your next steps are for improving your Incident Response readiness.
Thales Cyber Services ANZ External Attack Surface Assessment will assist your organisation to uncover exposed and forgotten assets.
Our methodology is designed to simulate what a real threat actor would focus on and will utilise similar tactics, techniques and procedures (TTPs) as a Red Team would do.
At the end of the engagement, you will receive a report that will outline your organisation’s attack surface.
Thales Cyber Services ANZ has a highly skilled and regarded technical assurance and testing team that has helped to detect risks and protect Australian and New Zealand organisations for many years across a wide variety of different industries. The knowledge they have uncovered has allowed companies across the ANZ region to enhance protection of their data and IT systems, brand and reputation.
Working with your business, security and IT team and other stakeholders, Thales Cyber Services ANZ can carry out a number of different adversary services. Our methodology can simulate what a real threat actor would focus on and use similar tactics, techniques and procedures to highlight where your vulnerabilities lie. Our experienced teams of penetration testers, red teams and threat analysts can find the chinks in your armor, help you bolster your detection capability and ensure you have robust plans in place to respond to cyberattacks.
At the end of the engagement, you will receive a detailed report, packed with actionable advice you can use to boost your organisation's security posture and ensure you are maximising the return on your information security investment.
Where a standard penetration test focuses on a single environment or system i.e. what’s in scope as identified by the organisation, a Red Team aims to be widespread i.e. everything identified by the Red Team (except anything flagged for exclusion by the organisation).
A Red Team simulates, within the bounds of their engagement, an Advanced Persistent Threat (APT). They often take far longer to plan and to execute than a tightly defined Penetration test.
A Red Team exercise challenges the full spectrum of your security operations. It provides a risk-managed approach to the organisation’s attack surface. In addition, the Red Team targets the human elements within a company, often neglected by annual security testing.
The “red team” is your attacking team. They are mimicking a potential real-life scenario and using the stealthy techniques a real adversary would use, trying to assess your organisation's cyber resiliency. A red team engagement takes planning and time – exactly as a real hacker would.
The “blue team” is your security team. They are being tested (usually without prior knowledge of the simulated attack), on their capacity to detect and respond to a situation.
In a “purple team” engagements Red Team and Blue Teams collaborate to plan and simulate tactics, techniques and procedures from known threat actors. The aim is to implement or improve your organisation's cybersecurity posture, usually targeting people, processes and technology but not limited to it. Gaps can be identified and closed in real-time.
“Gold team” exercises test your crisis management team – across the organisation, not just IT. It might also involve Legal, PR and other business divisions. It is a tabletop exercise designed to test crisis management policies and procedures and how well the crisis team communicates and executes.
Speak with a Thales Cyber Services ANZ Adversary Services consultant today to help determine the right service for your organisation.
Thales Cyber Services ANZ is a full-service cybersecurity and secure cloud services provider, partnering with clients from all industries and all levels of government. Let’s talk.