Posted by
Share this article
The goal of a Red Team exercise is to simulate what might happen in the event of a real-life hack against your organisation. It aims to provide your defensive team with an opportunity to react to a real adversary, exercising your technical mitigations, putting your detection to the test, and practising your incident response procedures. The red team exercise typically runs with specific goals and targets for the red team and without the prior knowledge of the blue team.
How does a red team exercise work?
Secrecy
In a red team exercise, your defensive team (or "blue team") should not be aware of the exercise. Ideally, only a small number of internal staff will be aware of the exercise, such as a Security Manager, CISO, or CEO. Because of this level of realism, you are able to obtain a better understanding of your security team's capability, and identify areas to improve or upskill. This type of exercise requires an engaged internal staff member (usually the security manager), who liaises with the red team during the exercise. The red team will keep the internal staff member apprised of major developments, so that in the unlikely event of an actual, concurrent cyber-attack, the red team exercise can pause, and the real threat be dealt with.
Depending on the goals of the engagement, the internal staff member can also subtly assist the red team, by giving suggestions about next steps, or providing limited internal information, to the red team. This does decrease the realism of the exercise slightly, but can dramatically increase the value of the exercise by providing meaningful stimulus to the blue team within the limited time of the engagement.
Planning and Scope
Initially, the red team will discuss goals and scope for the engagement. This should be a business-related goal - for example, attempting to gain access to a particularly sensitive database. It should define the particular scenario for the engagement, such as an external attacker, or a malicious insider. It should also specify whether certain threat types (e.g. physical access to your premises) is allowed. Usually, a thorough red team exercise should not limit the scope, because a real adversary would not limit themselves.
The test team will then attempt to achieve the goal, by whatever means have been allowed - phishing, exploitation, or even physical access.
Red Team Process
Once the engagement begins, the attack team starts with reconnaissance: identifying assets, staff members, and any information that might help target future attacks. Once a possible weak point is identified, the team will attempt to exploit it. If successful, the attack team will use this new access to perform more reconnaissance, and further exploitation towards the target.
In the event the red team is successful, and hasn't been detected, the team may (in liaison with the internal staff member), start performing more "noisy" attacks, to provide the blue team with opportunities to respond to the ongoing attack.
Who is red team testing suitable for?
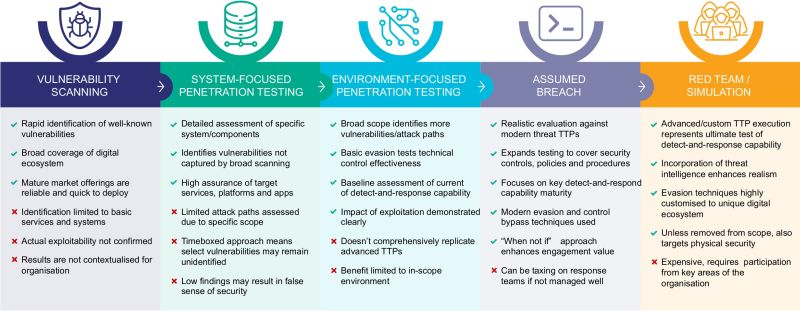
Any organisation that has valuable ICT assets can be a target for hackers. Red team testing is the natural next step in testing your defences against hacking attempts after running automated and penetration tests.
Red team exercise vs penetration testing
Red team exercises and penetration testing are complementary, as they each have different goals.
In a penetration test, the defensive team is typically aware of the exercise, so as to provide support to the testers, and give them as much information as possible, and deliberately bypass certain mitigations so that each layer of defense can be tested. While this makes for a more efficient test of the technology, it doesn't provide an opportunity for your defensive ("blue") team to practice their processes, or gauge their response to a realistic threat.
In a red team exercise, a key goal is to provide a stimulus for your defensive team to practice against. This is rarely a goal of a penetration test, nor is it usually even possible, due to a defensive team's awareness of penetration testing.
Whereas a penetration test is usually targeted at a particular system or limited scope, a red team exercise should not be limited. By allowing a broad scope, the attack team can identify weak points in the security of your organisation, much like how a real attacker would behave. This doesn't mean a red team can entirely replace a penetration testing program, as its goal is not to be comprehensive, but rather, to find weak points quickly. Penetration testing is still important to provide a comprehensive review of individual systems.
How Thales Cyber Services ANZ Can Help
By mimicking a real cyber-attack, Thales Cyber Services ANZ’s red team engagement, part of our adversary services, will provide your organisation with a detailed snapshot of the current level of your cyber resilience, covering your people, processes, and technology. The report will guide you on how to prioritise improvements to your detection and response capabilities to help your company stay ahead of adversaries.
Written by Richard Smith
Contact us
Speak with a Thales Cyber Services ANZ
Security Specialist
Thales Cyber Services ANZ is a full-service cybersecurity and secure cloud services provider, partnering with clients from all industries and all levels of government. Let’s talk.




