Posted by
Share this article
Operational Technology (OT) is the custom hardware and software that manages, controls, and monitors complex, single-purpose industrial machinery. This custom hardware and software components are called Industrial Automation and Control Systems (IACS) or Industrial Control Systems (ICS). OT is found across various industries including critical infrastructure ( energy, utilities, rail operations, telecommunication, etc.), healthcare, mining, manufacturing, and other safety-critical environments.
What’s the Difference Between IT and OT Security?
IT Security
IT security governs business-grade hardware and software, including devices, networks, and environments, as well as cloud and virtualised infrastructure, with user and workload management. The types of workloads covered by IT security include workplace applications, websites and apps, analytics, transactional workloads, virtual machines, and containerised apps.
The goals of IT security are data confidentiality, integrity and availability, via secure operations by authorised users.
OT Security
OT security governs devices, networks, and environments incorporating operational technology components. OT components are industrial devices and systems that blend physical and digital technologies and are designed for a specific purpose, such as a data collection unit in a mine, a building management system, or a complex medical device. OT comprises critical systems that must be operationally safe and reliable above all else, with some systems requiring 24/7 operations. A security failure in OT can cause serious harm, including human safety incidents and significant operations disruptions.
The goals of OT security are safe and reliable operations of industrial devices and systems, including secure operations by authorised users. Some OT devices and systems require specific management under industry regulations such as the Critical Infrastructure Act 2018 (SOCI).
OT vs IoT security
Internet of Things security governs the use and management of IoT devices within an environment. While these devices are built for a single purpose, and blend physical and digital technologies, they are not considered critical for safety and reliability like OT devices. Instead, IoT devices are consumer or business-grade devices that can be managed by business IT security, such as an RFID system for tracking company devices or smart lighting control in the office. Security failures with IoT devices and systems can be inconvenient and expensive but are highly unlikely to cause serious harm. The goals of IoT are the same as IT; with an extra focus on device-level data collection and transmission.
Where IoT security fits into OT
The Industrial Internet of Things (IIoT) refers to specialised IoT devices for monitoring OT environments. As high security is critical for OT environments, it stands that IoT deployed here must meet more stringent security requirements than their consumer or business grade counterparts.
IT and OT convergence
Previously, OT devices and systems existed on fully isolated networks, helping ensure the most secure operating environment. On-site SCADA (Supervisory Control and Data Acquisition) and DCS (Distributed Control System) systems provided the interfaces for remote, real-time streaming and analytic data of OT, requiring security solutions on both ends. Modern systems may now integrate IIoT, cloud SCADA and edge solutions, which only increases the complexity of security required to manage OT, and leads to more IT and OT convergence.
Why is OT cyber security important?
The threat to Critical National Infrastructure (CNI) and critical manufacturing is on the increase, with 93% of industrial organisations experiencing an OT incident in the past year, with 78% of these experiencing more than three intrusions. Businesses and suppliers must act with urgency to avoid major attacks. With OT in critical infrastructure or safety-critical environments, physical-cyber security is even more important.
How can OT cyber security be accurately governed?
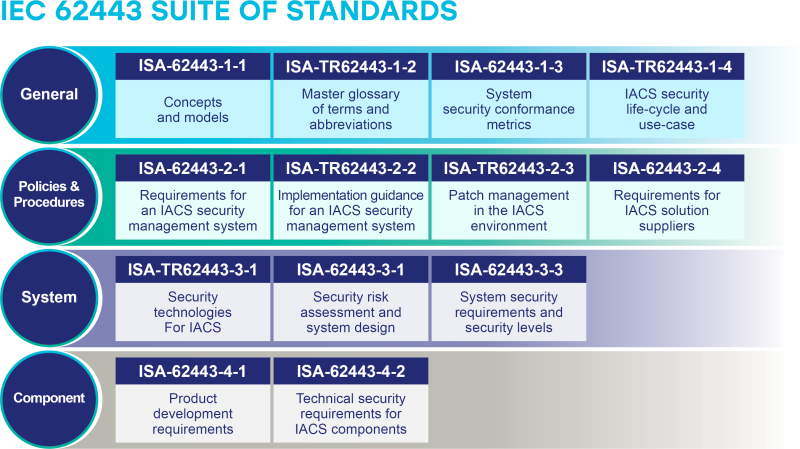
Thanks to the internationally recognised standards such as the ISA/IEC 62443 Series of Standards for Industrial Automation and Control Systems and the NIST Guide to OT Security 800-82r3, OT organisations can develop a solid foundational cyber framework, accurately assess risks, design secure systems and controls, and uplift their cyber maturity.
How can Thales Cyber Services ANZ help?
As Australia’s leading provider of full-service cybersecurity services in Australia and New Zealand, Thales Cyber Services ANZ is helping OT businesses increase their cyber maturity. Our OT Advisary services include comprehensive reviews of all systems and documentation, including site visits and deep investigation. Our reports are structured to deliver clear, actionable takeaways and detailed architectures where required.
OT Cyber Security Management System Uplift
Our uplift service establishes an Operational Technology (OT) and Industrial Control System (IACS) Cybersecurity Program, leveraging the IEC 62443 series of standards or the NIST Guide to OT Security.
OT Security Risk Assessment
Our comprehensive IACS risk assessment across your systems is aligned to IEC 62443 Part 3-2: Security Risk Assessment for System Design.
Security Level Assessment for OT Technical Controls
Our technical control assessment verifies the effectiveness of your OT technical controls deployed within IACS systems and components, as outlined in IEC 62443 Part 3-3: System Security Requirements and Security Levels.
Industry-specific coverage
Our services can be tailored for sectors and industries that have specific OT cybersecurity frameworks, guidance or directives, including:
- Critical Infrastructure Act 2018 (SOCI)
- Australian Energy Sector Cybersecurity Framework (AESCSF)
- TS50701 Railway applications cybersecurity: an international framework for trains and rail operations
- Water Services Association of Australia (WSAA) Cyber Security Resilience Primer-For Directors and Executives
- Transport Security Amendment Bill 2022
Extended ISA/IEC 62443 Coverage
Available upon request, including:
- OT asset discovery
- Patch management in the IACS environment
- Implementation guidance for asset owners
- IACS security lifecycle and use-cases
- Security system conformance metrics
- Product security development lifecycle requirements
Operational Technology Security Best Practices
- Apply appropriate frameworks, including the ISA/IEC 62443 standards for Industrial Automation and Control Systems (IACS).
- Establish a customised risk management framework for decision-making within OT environments.
- Establish an OT security program and stakeholders, including cross-functional OT/IT security teams.
- Define and manage zoned networks and assets to protect critical assets and infrastructure.
- Document all security controls for visibility traceability and to support easy troubleshooting.
- Deploy targeted security tooling, including logging, to effectively monitor and defend complex OT environments.
- Use maintenance and patch management solutions to ensure systems remain secure despite their age.
- System design assessments are used to ensure systems are verifiably secure by design.
- Establish a security training program to convey to all personnel who have access to any OT systems.
- Develop incident response and disaster recovery strategies to minimise the impact of a security incident.
For more information, see NIST Special Publication 800-82r3, Guide to Operational Technology Security.
Contact us
Speak with a Thales Cyber Services ANZ
Security Specialist
Thales Cyber Services ANZ is a full-service cybersecurity and secure cloud services provider, partnering with clients from all industries and all levels of government. Let’s talk.




