Essential Eight Compliance Services
We'll work with your team to assess your Essential Eight compliance, establish a baseline against the required standard and work towards compliance where required.

We'll work with your team to assess your Essential Eight compliance, establish a baseline against the required standard and work towards compliance where required.
The Essential 8 is a suite of strategies developed by the Australian Cyber Security Centre (ACSC), designed to mitigate the most common cyber threats that lead to security incidents and disruptions. Thales Cyber Services ANZ's Essential 8 compliance services encompass a broad spectrum of cybersecurity measures, applicable across various networks, systems, and applications, with a particular focus on Microsoft Windows-based networks. These services are not just about implementing security measures; they are about building a robust cybersecurity framework that enhances the protection of critical information and data.
How we can assist:
Understanding the Essential Eight
The Essential 8 Maturity Model
Why does Essential Eight matter to your organisation?
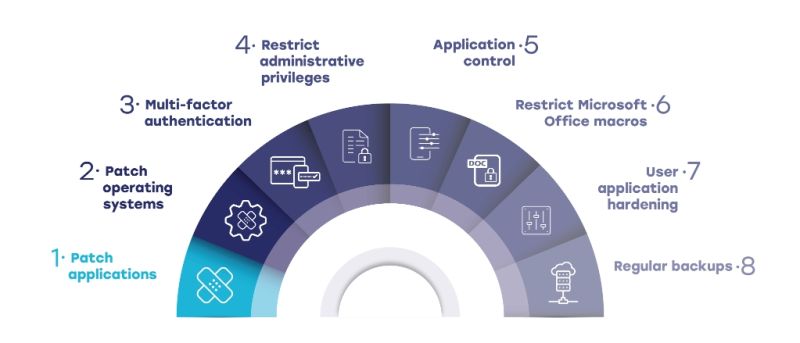
The Essential 8 is a set of mitigation strategies, developed and maintained by the Australian Cyber Security Centre (ACSC), that are designed to help organisations of all sizes protect themselves from the online threats that are recognised as being the root cause of most intrusion events and unplanned outages.
These cybersecurity advisory services can be applied across a broad spectrum of networks, systems and applications, from local installations through to cloud and other online services - although it is largely targeted at Microsoft Windows based networks. Essential 8 provides the building blocks of a robust cybersecurity strategy.
Each element of the Essential 8 focuses on a different aspect of cybersecurity strategy: the eight core elements identified as the most common areas resulting in cybersecurity incidents. The Essential Eight provide information and data management strategies, and guidance on secure configuration, to protect the confidentiality, integrity and availability of an organisation's critical information and data. The Essential 8 focus areas are:
Application control
Patch applications
Configure Microsoft Office macro settings
User application hardening
Restrict administrative privileges
Patch operating systems
Multi-factor authentication
Regular backups
Navigating the ever-evolving digital landscape can feel like venturing into a dense forest without a map. Cyber threats lurk behind every tree, and one wrong step can compromise systems. But fear not! There's a guiding light for Australian organisations: the Essential 8. Developed by the Australian Cyber Security Centre, this set of essential mitigation strategies offers a blueprint to significantly enhance an organisation's security posture and reduce the risk of cybersecurity incidents.
When it comes to combating cyber threats, generic solutions don’t cut it. Recognising this, the Australian Cyber Security Centre has developed prioritised mitigation strategies tailored to tackle various cyber threats effectively. This guidance was born from a comprehensive assessment of prevalent cyber security incidents. The result? The Essential 8 - a robust set of strategies to mitigate cyber security incidents.
Application control ensures that only approved applications run within systems. This reduces the risk of malicious code infiltrating the organisational network.
Regularly updating your applications and operating systems is like fixing the cracks in your house’s walls. By patching applications, organisations protect themselves from known security vulnerabilities.
Microsoft Office is synonymous with daily business operations. But malicious actors often exploit Microsoft Office macros. Tweaking the macro settings restricts the execution of potentially harmful code.
This is about fortifying your defenses. User application hardening limits the functions of applications, making it harder for adversaries to exploit vulnerabilities.
It's vital to ensure that only trusted individuals have access to privileged accounts, reducing the risk of malicious internal actions.
By implementing multi-factor authentication, organisations add an extra layer of protection, ensuring that even if passwords are compromised, malicious actors can't easily gain access.
Daily backups ensure that vital data remains secure and available, even if primary systems are compromised.
Web content filtering screens out malicious web browsers and pop-ups, ensuring that users don't inadvertently welcome cyber threats into the system.
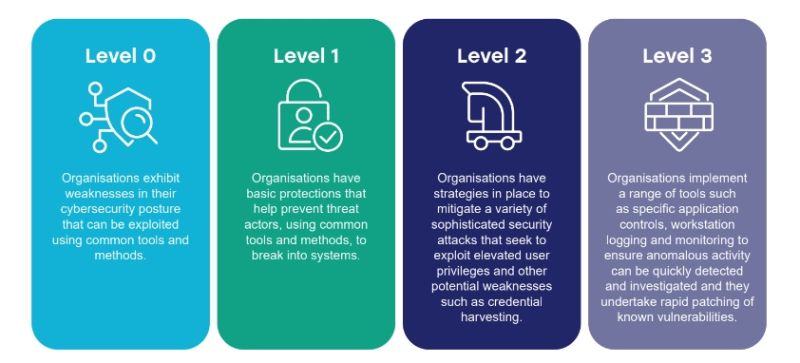
As well as providing guidance on what Australian organisations should do to reduce the risk of a cyber-attack, and how to minimise the impact should a threat actor breach your defences, the ACSC has created the Essential 8 Maturity Model to assist organisations in assessing how well they are implementing the mitigation strategies.
Level 0: At this level, organisations exhibit weaknesses in their cybersecurity posture that can be exploited by threat actors using common tools and methods.
Level 1: Organisations at this level have basic protections in place that help prevent cyber criminals and other threat actors, using common tools and methods, to break into systems.
Level 2: Organisations that achieve this level of maturity have strategies in place to mitigate a variety of sophisticated security attacks that seek to exploit elevated user privileges and other potential weaknesses such as credential harvesting.
Level 3: The highest level of maturity: these organisations implement a range of tools such as specific application controls, workstation logging and monitoring to ensure anomalous activity can be quickly detected and investigated and they undertake rapid patching of known vulnerabilities.
Cyber crime is on the rise. Every organisation faces a variety of threats ranging from highly disruptive and destructive ransomware attacks, to online fraud and the theft of data. Threat actors have at their disposal a vast array of tools and methods they can use to identify and exploit vulnerabilities to your systems.
Building a strategy to defend against these adversaries requires a strategic focus. Otherwise, it can seem impossible to detect and block each different type of attack. The Essential Eight provides a strategic framework that can be used to build a baseline defence against the cyber risks your organisation faces.
The Essential Eight matters to your business because it provides the building blocks of robust cybersecurity solutions that cover defensive measures to mitigate the risk of a breach and minimise the chances that a threat actor can compromise the confidentiality, integrity and availability of your data. Even at Essential Eight Maturity Level 1, organisations will be able to actively prevent many threats.
For government agencies, compliance with the Essential Eight is mandated. Many government agencies require that their suppliers also report on their Essential 8 measures. And while mandates are not in effect yet for commercial entities and the Not-For-Profit sector, we can expect Essential 8 compliance to become an emerging industry standard, as have ISO27001 and the NIST Cyber Security Framework.
In October 2024, The Defence Industry Security Program (DISP) announced changes to their cyber and assurance requirements as part of their DISP membership.
Defence Industry Security Program (DISP) maintains an active assurance and uplift program. The assurance program ensures DISP members meet and maintain their security responsibilities commensurate to their DISP membership requirements. The recent changes to DISP Essential 8 Cyber Standards Uplift Program looks to bring DISP in line with the latest recommendations by ASD for strengthening cyber security and to expand the DISP Cyber Security Standards to encompass the full Essential 8 at Maturity Level 2.
Our dedicated Essential 8 and Technical Practice team specialises in Essential 8 Assessments and Technical Uplift. Having been a trusted partner of the ACSC, we have successfully delivered similar projects for the Federal Government as part of their cyber uplift initiatives. With a team of over 40 Federal Government Security Cleared staff located across major capital cities, we are well-equipped to conduct technical assessments of your environment and strengthen your security posture.
Thales Cyber Services ANZ has deep expertise assisting both government and private organisations to implement relevant Essential Eight controls contextualised to our clients’ environments. Our proven methodology is based on a solid partnership with our clients. We start by understanding your goals and your specific cyber risks and threats.
Baseline: a current state assessment of your current controls
A baseline is established so that the current state of cybersecurity controls in your organisation are understood and assessed against the Essential Eight Maturity Model. You’ll work closely with Thales Cyber Services ANZ’s security experts, to identify where your strengths and weaknesses are.
Develop a roadmap to implement the Essential 8 controls
Our team of Advisory consultants will develop a plan to bridge the gaps between your current state and the right level of Essential Eight maturity required for your organisation.
Assistance with executing the roadmap recommendations
Once the strategic plan is agreed, Thales Cyber Services ANZ will leverage its team of over 400 cybersecurity experts to help you choose the best risk mitigation tools and strategies and help you to deploy them for maximum protection.
Essential 8 Assessment and Technical Uplift
Thales Cyber Services ANZ understands that there is no ‘one size fits all’ way to implement cybersecurity controls. We'll consider your organisation's objectives and needs and develop a bespoke solution that will deliver significant uplift in your organisation’s security posture. Thales Cyber Services ANZ, Australia's trusted cybersecurity company will work alongside you as your security partner to help ensure your people, systems, data and customers are protected.
Thales Cyber Services ANZ is a full-service cybersecurity and secure cloud services provider, partnering with clients from all industries and all levels of government. Let’s talk.