Digital Forensics and Incident Response
Turn uncertainty into clarity with expertise. Our incident response team are here to help you through this.

Turn uncertainty into clarity with expertise. Our incident response team are here to help you through this.
Our Digital Forensics and Incident Response team is equipped with the expertise, tooling, and processes to act decisively when incidents occur.
How we can assist:
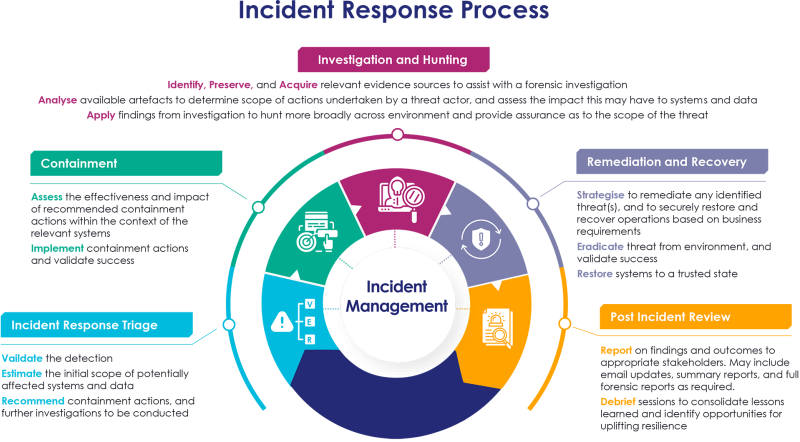
Our Approach to Incident Response
Our Digital Forensics and Incident Response team is equipped with the expertise, tooling, and processes to act decisively when incidents occur.
Let us handle the technical investigations, incident coordination, and reporting to help alleviate the stress and chaos of an incident, and get your organisation back to what you do best.
Interested in improving your incident resilience?
Our DFIR team also distil the experiences and intelligence from the front-line of cyber defence into relevant and practical advisory, to make sure when an incident hits, your organisation is best prepared to handle it.
Local support and advice, as well as guaranteed response time in the event of an attack.
Incidents are inherently stressful and chaotic times.
Cyber incidents are rarely simple. Beyond the technical disruption, it’s the orchestration of response, across teams, systems, and stakeholders that defines the true complexity of a crisis. When an organisation is under pressure, the ability to coordinate effectively becomes as critical as the digital forensic investigation itself.
During an incident, organisations face a convergence of unknowns. Staff are diverted from core responsibilities, visibility is obscured, and internal and external stakeholders demand clarity and control. The pressure to deliver answers fast and accurately can overwhelm even mature teams.
Cyber incidents introduce uncertainty, urgency, and disruption. While technical investigation is essential, the broader challenge often lies in managing the operational and strategic response across the organisation.
Organisations under pressure must navigate:
In these moments, the ability to coordinate effectively becomes critical. Without alignment between technical teams and executive leadership, even high-quality forensic work may not translate into effective outcomes. Delays in communication or misinterpretation of findings can lead to decisions that increase risk or prolong recovery.
In 2025, organisations operating in Australia and New Zealand face increasing regulatory scrutiny around cyber incident response:
Cyber Security Act 2024 (Australia): Introduced mandatory ransomware reporting for businesses with annual turnover above AUD $3 million. Minimum security standards for smart devices are also being phased in.
Cyber Incident Review Board (CIRB): Established under the Cyber Security Act 2024, Commenced on May 30 2025, significant incidents may be subject to independent post-incident reviews, requiring organisations to maintain detailed forensic records and response documentation.
Advance network assessments for attack scenarios.
Our Incident Response Retainer ensures your organisation has access to specialist incident response support governed by a defined Service Level Agreement (SLA), enabling alignment with insurance and regulatory expectations. Minimising response delays by completing onboarding and environment familiarisation in advance, allowing for immediate escalation and streamlined resolution when incidents occur.
Have a suspected incident but don’t know where to turn?
Our DFIR team is experienced in dropping into the middle of incidents, rapidly assessing the situation, and helping to take control of the matter. _For our ad-hoc customers, there is no SLA for response time nor will we have had the chance to understand your incident response processes or operational needs. However, our team are still adept at rapidly coming up to speed and will work to a high degree of excellence to get you back where you need to be.
A retainer allows us to understand how your organisation operates in an incident, and help uplift your overall cyber incident resilience.
On top of having an SLA for response times, our retainer partnership model focuses on collaborative efforts to build your resilience through work such as Incident Response Plans, Operational Playbooks, Compromise Assessments, and Incident Response Scenario exercises._
Rather than be simply a phone number to call, we strive to be an augment to your team, not only as incident operators but as trusted advisors to help shape your incident response and resilience strategy. To this end, our commercial model is based on rewarding our partners who invest more into their resilience uplift with better rates.
Forensic Services
Pre-Incident Resilience
Incident Response
Be Proactive About Your Cyber Resilience.
Organisations must move beyond static plans and embrace dynamic, scenario-based preparation to ensure readiness across executive and technical teams.
Align Your Response Strategy with Real-World Threats and Industry Standards
An effective incident response plan is more than a document—it’s a living framework that must reflect your organisation’s threat landscape, internal capabilities, and regulatory obligations. Thales Cyber Services offers a structured review process to ensure your IR plan is fit for purpose.
What’s included:
Following the review, we provide actionable recommendations and, if required, support the creation or update of your IR plan to align with best practices and compliance requirements.
This service helps organisations ensure their response strategy is not only comprehensive but also executable under pressure.
Validate Plans, Strengthen Coordination, and Identify Gaps Before a Real Incident
Thales Cyber Services facilitates immersive tabletop exercises that simulate realistic cyber-attack scenarios tailored to your organisation’s environment. These sessions engage key stakeholders—including IT, legal, communications, and executive leadership—in role-based decision-making and strategic response.
Key benefits include:
Exercises are designed for both executive and technical audiences, with tailored scripts and scenarios such as ransomware, phishing, data breaches, and malware attacks. Dual-group formats ensure consistency in evaluating readiness across the organisation.
Test Real World Threat Scenarios and Strengthen Response Capabilities
Simulation workshops go beyond theory, challenging teams with live, scenario driven exercises that reflect current threat patterns and attack vectors. Thales incorporates “curve balls” to test assumptions and uncover hidden vulnerabilities. This can take different formats:
Key benefits include:
These simulations help organisations benchmark their maturity, refine playbooks, and build confidence in their ability to respond swiftly and effectively.
See our different types of exercises available below:
Operational Decision Making Exercise:
Methodology - Discussion based exercise walking through a scenario to discern operational decisions and procedures, to ensure familiarity with playbooks.
Effort/Cost - Minimal
Operational Live Test-Drive Exercise:
Methodology - Using production tooling and assets with no simulated events, but stepping through the actions required in operational playbooks within each platform to ensure familiarity.
Effort/Cost - Low
Operational Offline Technical Exercise:
Methodology -No production tooling and assets, using extracts and artefacts relevant to the environment to assess operational familiarity.
Effort/Cost - Medium
Operational Production Technical Exercise:
Methodology - Using live production tooling, simulate an incident. Typically on a single endpoint or server with minimal technical impact on the rest of the environment. Good for testing SOPs for small scale incidents.
Effort/Cost - High
Operational Replica Production Technical Exercise:
Methodology - Using a replicated production environment, simulate a critical incident that results in outages and significant impact on the rest of the environment.
Effort/Cost - Very High
A good incident investigation is informed by the key questions they seek to answer. However, these questions aren’t always up to the organisation to define. With the regulatory landscape changing (particularly in recent times with changes to mandatory data breach reporting, and ransomware reporting), knowing how to respond to and engage with these stakeholders is critical to an effective response.
Even for investigations which can be handled with in-house security or IT teams, depending on the circumstances it is often prudent to consider engaging a third party to conduct an independent investigation and report.
Similarly, in a legal context should you suspect any legal disputes from the result of an incident (for example, if you are unable to satisfy a contractual obligation due to an outage as a result of the incident), it’s important to engage a third party firm. We regularly work with law firms and in-house legal teams to ensure investigations and reporting is handled to the high standard required in these circumstances.
Aside from regulators and lawyers, dealing with insurers is another important consideration. Even if you do not hold a specific cyber insurance policy, if you suspect a claim may be made on some other policy (for example, business interruption), having an external firm attesting to the report is important.
At Thales, we integrate global expertise with local insight to deliver cybersecurity services that go beyond conventional models. Our approach is built on operational depth, strategic collaboration, and vertical specialisation designed to support resilience before, during and after incidents.
Incident Response and More
We unlock the full of our DFIR team to support your organisation in not just technical analysis and investigations, but through deep experienced Incident Coordination/Management capability tying everything together. Outside of an incident, our DFIR team is also available to help make your organisation Incident Response ready and resilient as possible.
Creating Partnerships
Rather than taking a "one size fits all" productised approach, we build enduring partnerships. We're here to support your end to end cybersecurity maturity, tailored to each organisation’s journey.
Deep Technical Expertise
Thales brings deep specialisation in critical infrastructure, defence, high tech/engineering, and other similar high-stakes environments. We are able to draw on niche technical skillsets and experience, allowing us to purpose-build solutions for the unique technology demands of your organisation.
Industry Threat Intelligence Collaboration
We actively collaborate across public and private sectors to strengthen Australia’s cyber posture. Our reciprocal threat intelligence and technical capability sharing reinforces our commitment to national resilience and industry wide uplift.
Running an effective Security Operations Centre.
The complexity of running your own 24/7 SOC can be a distraction from your business’s core purpose. Avoid the hassle of coordinating IT resources, maintaining compliance and managing your security in a comprehensive, cost-effective way by partnering with us.
Managing your security program.
Being in control means having the right information at the right time. A good detection and response program will ensure you maintain the highest standards across your Governance, Risk and Compliance (GRC) activities. Our IT security experts offer decades of experience dealing with breaches of varying sizes and scales.
Detecting and responding to common threats and attacks.
The greatest challenge for businesses today is the rapid detection and response to threats. Malicious attacks, including malware, phishing, ransomware, DDoS and social engineering attacks can escalate quickly, becoming a major breach. The PR and regulatory implications can be devastating. We bring together the right people, processes and technology to protect your organisation.
CISO’s, CIOs and third-party SOC providers are required to perform notifications to the regulator about incidents. This would involve determining whether the incident affects a critical infrastructure asset, providing details and description of the cyber security incident within 12 hours and then a written assessment within 72 hours for provision to the regulator.

An Incident Response Retainer offers a process of forensic discovery, active containment, and rapid eradication of intruders from the network. Gain access to incident response experts and secure guaranteed SLAs.
Thales Digital Forensics and Incident Reponse Team have several SLA options available as part of our DFIR retainer offerings – with a contracted response time as low as 2 hours. However, we strive to respond as quickly as possible and depending on timing of the initial enquiry, often respond within the hour.
Our expertise spans across government, critical infrastructure, not for profit, multinationals, and small-to-medium enterprises.
Our pricing is tailored for business-to-business (B2B) engagements, ensuring value and scalability for organisations of all sizes. However, we may also be able to support individual clients depending on the scope and nature of the request. Get in touch to explore how we can help.
Thales Cyber Services ANZ follows the NIST 800-61 framework when dealing with major cyber security threats in our customers' environments.
The framework consists of the following steps:
Preparation – Thales Cyber Services ANZ’s proactive approach to incident response delivers your organisation an incident response plan, ensuring those responsible for participating understand their roles and responsibilities and that your organisation has a plan in place when the worst happens. Preparation is a proactive measure that has the biggest influence on reducing the impact of cyber incidents whilst assisting to prevent an incident in the first place.
Detection – Thales Cyber Services ANZ assists in ensuring that your organisation will not only have the appropriate security tools in place, such as SIEM and EDR but that the information being collected is relevant and in line with best practice, assuring protection of the data that matters to you and keeping your security solution cost-effective. In addition to providing skilled analysts and engineers, we also arm them with advanced threat detection tooling and techniques such as AI and automation.
Analysis – Thales Cyber Services ANZ analyses security alarms, events, and incidents to deliver end-to-end incident response for your organisation. Our team of specialists analyses an incident to determine the source, how best to remediate it, and to confirm remediation steps are complete using a combination of automated and manual techniques.
Containment and Eradication – Containment and Eradication without the appropriate skills can result in further organisational damage - critical data may be deleted, or assumptions made on the ‘eradication’ of a threat actor, when they may still be active elsewhere, or commonly, have placed back doors in your environment to regain access. Thales Cyber Services ANZ has the skills to contain and eradicate major cyber security incidents to their entirety. Thales Cyber Services ANZ can also conduct digital forensic analysis when required.
Recovery – Thales Cyber Services ANZ supports organisations in recovery through post-incident reviews, recommendations for improvement to prevent the recurrence of incidents, and supporting documentation reviews.
Post Activity – Thales Cyber Services ANZ will carry out any further digital forensic activities as requested by the Customer, including providing reporting aligned with your governing body or federal government guidelines. Thales Cyber Services ANZ has the capacity to speak in court if your incident becomes a legal matter.
Thales Cyber Services ANZ is a full-service cybersecurity and secure cloud services provider, partnering with clients from all industries and all levels of government. Let’s talk.