Penetration Testing
Protect your digital assets: ensure your organisation’s defences are effective.

Protect your digital assets: ensure your organisation’s defences are effective.
Thales Cyber Services ANZ's penetration testing discovers hidden vulnerabilities before attackers do. Think of us as your cybersecurity SWAT team, uncovering weaknesses and simulating real-world attacks to fortify your defences.
Exposing security gaps before they're exploited by malicious actors.
Prioritising remediation efforts based on actual risks.
Boosting confidence with a proven penetration testing methodology.
Meeting compliance requirements with industry-standard testing procedures.
Don't wait for a breach to expose your vulnerabilities. Our ethical hackers put your systems to the test, to ensure your organisation's critical data is protected.
How we can assist:
Infrastructure Security Assessment
External Infrastructure Penetration Test
Whether it’s hosted in the cloud, internally, or externally, we have multiple scenarios to simulate an attacker who might attempt to breach your network.
Thales Cyber Services ANZ technical assurance & testing services infrastructure assessments will assist your organisation in identifying exploitable vulnerabilities that may be found in your network.
Whether you are looking to meet compliance requirements such as PCI or ISO27001 or want to have a better understanding of your current attack surface, Thales Cyber Services ANZ security experts can assist you to ensure you not only meet those requirements, but will validate that your current defence posture holds up against a cyber-attack.
Threat actors continuously probe systems searching for vulnerabilities they can exploit in order to steal data, compromise the operation of systems or damage your organisation's reputation. The definition of external penetration testing is to employ similar tools, tactics and procedures as malicious parties to search for potential weaknesses.
External penetration tests assess public-facing systems by simulating a malicious attacker on the internet. Public-facing systems include servers that have public IP addresses which can be accessed by users on the internet, such as websites and email servers.
External penetration testing uses tools and methods that can detect issues such as identifying firewall misconfigurations, identification of unpatched vulnerabilities and locating and compromising administrative services and interfaces.
Thales Cyber Services ANZ has extensive experience in using external infrastructure testing methodologies to look for various security flaws. These methodologies include:
The testing will determine potential attack vectors by which a system could be compromised remotely. Thales Cyber Services ANZ will present the findings with reproduction steps, along with recommendations around remediation.
We recommend External Infrastructure Pen Testing be conducted annually, or at least after any major network changes to internet facing systems and services.
Thales Cyber Services ANZ External Infrastructure methodology uses both manual and automated testing of your organisation’s public-facing infrastructure (for example websites and email servers) to determine if an external attacker can breach your perimeter.
External penetration testing will allow your organisation to validate how your current cybersecurity solutions hold up against an external attack.
With compliance now a major issue for organisations to manage, external penetration testing carried out by an expert independent party can assist with remaining compliant with established regulations and security standards. For example, the Australian Prudential Regulation Authority (APRA) requires the organisations it oversees to conduct independent external penetration tests annually. Security standards such as PCI DSS require penetration testing (external and internal infrastructure) to be compliant.
What is internal penetration testing?
Penetration testing simulates an internal attacker such as an employee or contractor who has access to your internal network or external intruders who have breached perimeter defences.
This is done by finding the attack path that a potential internal threat actor could use to gain access to sensitive data from your organisation’s internal network. This includes file servers, workstations, and applications. As well as finding how a malicious party can exploit internal systems and network weaknesses, internal penetration testing can find threats that emanate from accidental errors made by staff that can lead to data exfiltration or other significant issues.
During an internal penetration test, an experienced tester will be given some access to your internal network. This is typically the same sort of access an ordinary employee has. The tester will attempt to escalate the level of privilege that account has with the intent of accessing data or systems that the account ought not be able to access. Or, the tester could use their escalated privilege to compromise network equipment in order to launch an impactful attack.
The Thales Cyber Services ANZ approach to internal infrastructure penetration testing is to simulate an internal attacker, potentially an employee or contractor, who has access to your internal network.
This is done by exploiting vulnerabilities and finding the attack path that a potential internal threat actor could utilise to gain access to sensitive data.
Your organisation’s internal network, (file servers, workstations, etc.), is exposed to threats from:
Organisations are encouraged to test the internal network at least as frequently as they do the external perimeter.
The Thales Cyber Services ANZ report generated as the output of this work is designed for both executive/board level and technical staff.
While significant attention is given to detecting and mitigating the risks associated with external attackers, internal penetration testing detects the risks of an internal actor with access to your network.
Internal pen testing gives your organisation an understanding of how an internal attacker could compromise your internal network and provide real insight into the potential damage and business risk an attacker could inflict.
As well as detecting technical issues, a penetration test can detect weaknesses in policies and procedures. This can include giving users unnecessarily escalated privileges, weak processes for assigning access to systems or poorly defined system access roles.
An internal penetration test ensures that your internal security posture is robust and that internal weaknesses are recognised and remediated.









Is your organisation conducting regular, scenario-based penetration testing to validate its resilience against cyber threats—as now expected under the SOCI Act’s risk management and cyber maturity obligations? We deliver comprehensive testing services—including Wi-Fi and wireless assessments, physical intrusion testing, red, purple, and gold teaming exercises, as well as internal, external, and application-layer penetration tests—ensuring your organisation meets its obligations under the SOCI Act through evidence-based security validation.

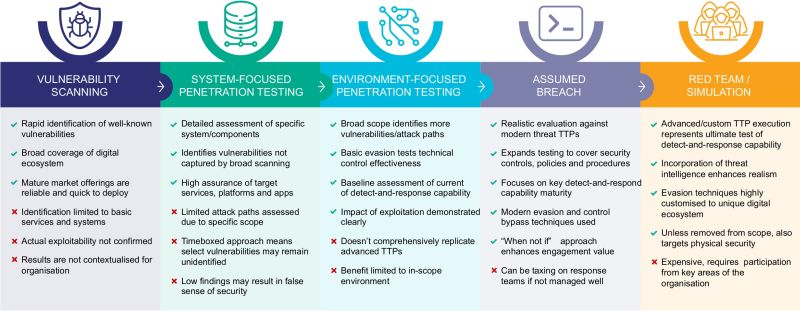
Explore some of the ‘quick wins’ exploited by both Red Teams and modern adversaries to gain privileged access within diverse digital environments.

Here are common things to look for when choosing a pen tester:
Find a company you trust
Trust is fundamental. You will be allowing this company to access your systems, customer data and sensitive company intelligence. In effect, you’ll be permitting access into the inner workings of your organisation’s operations. Be sure that they can be trusted with your data and they have a proven track record. When was the company established and how many penetration tests they have performed for large security focused organisations? Ask if they have worked with clients in your industry sector and can provide references.
Can they meet my brief, or help me define it?
To get the best value for your IT security investment, you need to know exactly where you need help, why and what you want security tested. The better the brief the better the job, so clearly define your objectives and outcomes from the start.
Are they able to answer my questions?
Ask questions about the testing methodology. What defined procedures and tools does the company use? How do they protect your business and data during the testing? How do they remove false positives? How many classes of testing are performed? How are complex multi-stage attacks covered?
Is the testing outsourced, sub-contracted or in-house?
Remember that a company does not conduct a penetration test, people do. No matter which company you go with, it always comes down to the person or the team you have working on your business. Find out who exactly will be conducting the testing, is it outsourced, sub-contracted or in-house? Ask to see their credentials and interview them by phone, Zoom or in person. Finally, ask if you can be provided with interesting findings as they occur throughout the testing.
Can they show you a typical report?
Up front, ask the company exactly what you will receive at the end of the penetration test. Ask to see what a real-world deliverable looks like. A quality report should detail the key findings and provide solid remediation advice, in priority order, to address every issue found. In short, the final report should be a valuable tool with a clearly defined action plan on the best ways to remediate vulnerabilities. Quality reports also detail how to re-test each vulnerability once the identified flaws have been fixed.
Almost all our assurance team is based in Australia and New Zealand. We do have some staff that work internationally, often because they have relocated for personal reasons but want to keep working with us. All our staff have gone through rigorous security checks.
Yes, we are proudly CREST ANZ certified.
Thales Cyber Services ANZ has extensive experience with complex architecture designs gained through years of experience working with clients of all sizes, industries and structures. As we are watching threat activity on a daily basis, We are constantly learning about the latest attack techniques, exploits and security flaws. Our external pen testing methodology covers:
Our Offensive security team follows OWASP, NIST SP 800-115, and CREST-aligned methodologies.
Penetration testing is a controlled security assessment that simulates real-world cyberattacks to identify exploitable vulnerabilities in systems, applications, or infrastructure. It helps organisations validate their security controls, reduce risk exposure, and meet compliance obligations.
Vulnerability Assessment identifies known weaknesses generally using automated tools that can be performed periodically. Penetration Testing goes further by actively exploiting vulnerabilities to assess real-world impact and validate risk. Usually a blend of manual and automated techniques. Our Thales Offensive Security team perform manual validation to reduce false positives, and find bespoke vulnerabilities that generic scanners would not find.
Each engagement is unique and tailored to your environment, and the agreed scope of work for testing. A penetration test is largely priced based on the estimated number of days required to complete the engagement.
We have conducted tens of thousands of penetration tests over the last two decades. We start by listening.
Pentesters usually aim to achieve the following qualifications and certifications to upskill themselves and display credibility:
Thales penetration testing services support:
SOCI Act
PCI DSS Requirement 11.3
ISO/IEC 27001
APRA CPS 234 & 230
Yes. Remediation testing (also known as retesting) is a critical follow-up service offered by Thales. It ensures that vulnerabilities identified during the initial penetration test have been properly addressed and no longer pose a risk.
To support deeper security maturity and uncover why vulnerabilities exist, we recommend bundling penetration testing with the following services Thales offers: Secure Code Review, Architecture & Configuration Review, Threat Hunting and Managed Detection & Response (MDR) and Security Awareness & Phishing Simulation.
Internet of Things (IOT) and Operational Technology (OT) Penetration Testing
Thales's IoT/OT penetration testing capability will assist you in understanding the resiliency of your IoT/OT ecosystem against cyber threats.
Offensive Security Services
By proactively seeking out and mitigating weaknesses before they are exploited, organisations can stay ahead of attackers and reduce the risk of data breaches and financial losses.
Thales Cyber Services ANZ is a full-service cybersecurity and secure cloud services provider, partnering with clients from all industries and all levels of government. Let’s talk.