Australia’s critical infrastructure regime establishes positive and enhanced security obligations over 11 industry sectors that have been deemed critical in providing services to Australians. These obligations when correctly followed improve the resilience of those businesses that operate Australia’s critical infrastructure assets, and in turn Australia. This is achieved through an “all hazards” risk approach, requiring entities to capture and consider risks across four key domains:
- Personnel
- Cyber
- Physical
- Supply Chain
Annually those businesses captured by the critical infrastructure regime are required to attest to the adequacy and appropriateness of their Critical Infrastructure Risk Management Program, requiring a look back at the year that was, and importantly, a look forward to the year ahead
Understanding the SOCI Act | How can we help | Our SOCI Team | Chat with Us | FAQs
Practical Approaches to Security Obligation | Resources
Attestation Date - Your Obligations
On 28th September 2025 a large segment of organisations captured by the legislation will be required to attest to the effectiveness of their risk management practices. This annual obligation requires that entities review their risk management programs. In advance of this, it is important that organisations begin preparation, including reviewing key data points and the design and operating effectiveness of their CIRMP, importantly, the engagement with Board stakeholders will help drive better organisational outcomes, while supporting directors to fulfil their professional duties and minimise the risk of delay in attestation completion.
What do I need to know?
Review your current asset portfolio relative to the SOCI requirements and Cyber and Infrastructure Security Centre (CISC) guidance, consider if anything has changed over the last 12 months.
The Cyber and Infrastructure Security Centre will not engage with you directly to advise entities that they are critical infrastructure in most cases. You need to review the critical infrastructure asset rules to see if any of your assets are critical.
Hint: We would suggest that if you were engaged that it is time to get prepared to be captured by SOCI.
Consider your timeframe for attestation and whether you have reviewed your assets, updated your risk management plan and have prepared your Board for attestation by 28th September 2025
Understanding Australia's Security of Critical Infrastructure Requirements (SOCI Act) & What They Mean For You?
Background on Australia's Critical Infrastructure Landscape
The Security of Critical Infrastructure Act 2018(Cth) (SOCI Act) introduced sweeping reform to the way Australia both views and manages its critical infrastructure assets. Since its inception the SOCI Act has continued to evolve to continue strengthening how we view and manage our critical infrastructure.
In 2021 and 2022 the SOCI Act was amended significantly to strengthen protections for Australia’s critical infrastructure amid an evolving threat landscape. This saw the SOCI Act expand its coverage of defined critical assets, introduced enhanced cybersecurity obligations, positive risk management obligations and a requirement to better understand internal and external supply chains and personnel. Importantly, it also enhanced cross-industry and industry – government collaboration.
What is captured as Critical Infrastructure?
The 2021 and 2022 amendments saw the number of industries captured by SOCI, expand, these are noted below.
- Communications
- Financial Services and Markets
- Data Storage or Processing
- Defence Industries
- Higher Education and Research
- Energy
- Food and Grocery
- Healthcare and Medical
- Space and Technology
- Transport
- Water and Sewerage
Strategically, these sectors have been identified as those physical facilities, supply chains, information technologies and communication networks, which if destroyed, degraded or rendered unavailable for an extended period, would significantly impact the social or economic wellbeing of the nation, or affect Australia’s ability to conduct national defence and ensure national security.
Source: Cyber and Security Infrastructure Security Centre, Security of Critical Infrastructure Act 2018 (SOCI)
Not all organisations within these sectors will have critical infrastructure assets, however all should have an understanding of why they do or do not. Importantly, all organisations within these sectors should have an understanding of their supply chains and the material risks to their strategic and operational objectives.
This point is of increased relevancy following 2024 amendments to the SOCI Act that see secondary assets that hold business critical data of primary assets captured, while also extending the obligations of telecommunication asset owners.
CISC Auditing
In November of 2024 the CISC commenced audits over Australia’s Critical Infrastructure asset operators, including those operators who it deemed to be critical, regardless of whether they have identified themselves as having critical infrastructure assets.
It is expected that these audits will become common place for entities in what is already a complex regulatory landscape with many competing priorities.
Integrating and optimising Critical Infrastructure Risk Management Programs can simplify this compliance burden.
Enforcement and Penalties
Penalties and enforcement options vary under the SOCI Act depending on the severity of the incident or contravention, however can go up to 250 civil penalty units.
The CISC may also compel entities to vary their critical infrastructure risk management programs, while also holding a range of other powers enabling their intervention in direct response to cyber security incidents. This may occur in instances where the impacted entity is unable or unwilling to address the issue themselves, however these intervention powers are reserved for emergency circumstances only.
Book an Advisory Session
Practical Approaches to Performing Positive Security Obligations
Meeting the requirements of the SOCI Act — including Positive Security Obligations (PSOs) and Enhanced Security Obligations (ESOs) — can be complex, especially given how deeply these rules impact the entire organisation.
A successful approach starts with clear stakeholder mapping and strong executive sponsorship to align security and business priorities. Understanding who the obligations apply to — from technical teams to business leaders — is key to building an effective, compliant security program.
The table below highlights each positive obligation and the common stakeholders responsible for delivering on them.
Item | Obligation under SOCI Act | Practice Performance | Key Stakeholders |
|---|---|---|---|
| 1 | Asset Registration (Part 2) | The asset registration process requires details of the assets’ ownership, location and operation to be lodged with the regulator through a web portal. Changes to ownership or operation require the portal record to be re-submitted within 6 months of the change. | GRC Site/Facility managers |
| 2 | Protected Information (Part 2) and Business critical data | Entity information security policy and information classification requirements should describe a process for defining, determining and managing protected information and business critical data and for engaging SOCI stakeholders if either data set is affected in an incident. For less mature organisations a definition of what constitutes these information types will be of value if policy does not already provide a table for information classification specifically covering these. | CISO/CIO |
| 3 | Data provider notifications (12F((3)) | Business critical information to be defined. GRC to notify data centres that they hold critical infrastructure asset data/business critical information. | GRC CISO/CIO |
To view the rest of the obligations and practical approaches, click here.
SOCI Data Amendments - What they mean and what you need to do?
The Security of Critical Infrastructure Act 2018 (Cth) (SOCI) was amended in late 2024 to capture the data storage systems that hold business critical data of those organisations captured under the Critical Infrastructure regime. In practice, this will also require entities to consider the risks to those data storage systems that are holding business critical data as part of their CIRMP, according to guidance from the Cyber and Infrastructure Security Centre this must occur before 28 May 2025.
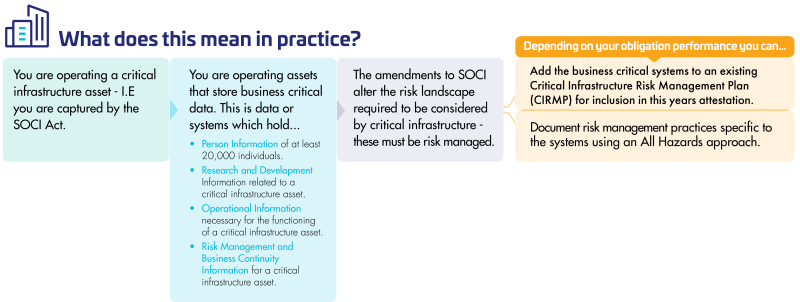
High Level Guidance
The Security of Critical Infrastructure Act 2018 (Cth) (SOCI) was amended in late 2024 to capture the data storage systems that hold business critical data of those organisations captured under the Critical Infrastructure regime. In practice, this will also require entities to consider the risks to those data storage systems that are holding business critical data as part of their CIRMP, according to guidance from the Cyber and Infrastructure Security Centre this must occur before 28 May 2025.
| Review data storage systems to understand which systems are business critical, undertaking a gap analysis between your existing requirements and amended SOCI requirements and SOCI to understand any uplift requirements. | Review the risk environment surrounding your business critical systems, including recent incidents, control testing and assurance reports, risk registers and outcomes of BCP testing, uplifting through risk workshops as required. | Adopt a low compliance risk appetite approach and develop or redevelop your CIRMP, aligning with better practice across CI entities. Review your current definition and application of ‘Business Critical Data’ against the legislative definition found in Section 5 of SOCI. |
Our Solutions to Meet SOCI Obligations
Thales Cyber Services ANZ (Formerly Tesserent) is a sovereign, critical infrastructure entity with a proud history of providing national security outcomes for Australia. We have been a sovereign partner to the Commonwealth for over two decades, stemming from its acquisition of Australian Defence Industries, which through its legacy companies, has provided sovereign military capability to the ADF for more than 100 years. Bound by an unprecedented Deed, Thales and the Commonwealth have a shared responsibility for the successful operation of industrial capability, strategic facilities and the handling of critical Intellectual Property in the interest of Australia’s defence and national security.
Consequently, we are in a unique position to advise on bespoke outcomes focused SOCI solutions that are fit-for-purpose and underpinned by value protection without unnecessarily impeding value creation as the only critical infrastructure asset operator who provides services to others.
We can support you through:
- SOCI Readiness Assessments
- SOCI Assurance
- Critical Infrastructure Risk Management Plan (CIRMP) Development
- Supply Chain Analysis & Mapping
- Cybersecurity services including:
- Risk, Resilience & Compliance Transformations
- Crisis Management Support
- Organisational resilience activities, including but not limited to:
- Business continuity testing
- Crisis management simulations
- Event simulations
- Business Continuity Plan Development
- Assurance Mapping
- Application and Data Security Compliance
If you’re unsure of how we can support you, please reach out for a chat. These are just a sample of the services that we offer to support your needs and we are available to develop an end-to-end advisory support solution that is tailored to your needs.
Our SOCI Team

Zoe Thompson
Portfolio Lead - Critical Infrastructure Resilience
Zoe is the Thales practice lead for SOCI. She supports clients captured by the Security of Critical Infrastructure Act or with Operational Technology assets to comply with regulatory regimes associated with critical infrastructure and best practice cyber security frameworks. Zoe has 20 years of security leadership experience. Her early career was spent advising the Australian Government, allied and close regional partners on national and cyber security issues and advancing Australian interests in the cyber and emerging technology space. Zoe then delivered security outcomes for Defence and Home Affairs portfolio agencies – performing numerous ISM and other framework assessments, leading programs of build and remediation to support.

Mitchell Loughlan
Partner - Critical Infrastructure Resilience
Mitchell is a Partner within our SOCI team and leads our GRC practice and supports our clients to develop, integrate and operationalise fit-for-purpose risk and governance practices to support their ongoing SOCI regulatory compliance. Mitchell is a former lawyer with extensive and diverse experience across the financial services industry, ASX 200 and leading government entities in delivering a range of risk, resilience and compliance advisory, regulatory change, governance and business optimisation programs. He has extensive experience in the simplification of complex regulatory requirements through concise but clear communication, while simplifying risk to deliver value and enable understanding across all levels of maturity. Prior to joining Thales, Mitchell worked within the Big Four and has held various roles within leading financial services and energy organisations, furthering his consulting experience to deliver hands on change and business improvement programs while working with executive peers, boards and external stakeholders to realise positive business outcomes. Mitchell brings extensive experience in the development, integration and operationalisation of Critical Infrastructure Risk Management practices, with a focus on their effective integration into business-as-usual practices to maximise efficiency while protecting value. Mitchell’s experience enables him to work with stakeholders across all business levels to support end-to-end understanding and awareness.
Resources
Guide | Critical Infrastructure and the Role of the Board in Managing Risk
View PDF
The Board plays a central role not only in the attestation process, but also throughout the year to ensure an organisation is implementing effective risk governance mechanisms and is identifying and managing all relevant risks.
Checklist | Critical Infrastructure Risk Management Program
Support your organisation’s compliance with confidence—ensure your oversight responsibilities are met ahead of the 28 September attestation.
Guide | Practical Approach to Positive Security Obligations
A successful approach starts with clear stakeholder mapping and strong executive sponsorship to align security and business priorities. Understanding who the obligations apply to — from technical teams to business leaders — is key to building an effective, compliant security program.
Frequently Asked Questions
What is the SOCI Act and why is it important?
The Security of Critical Infrastructure Act 2018 (Cth) (SOCI Act) establishes positive and enhanced risk and security obligations over 11 industry sectors that have been deemed critical in providing services to Australians. These obligations, when correctly followed, improve the resilience of businesses that operate critical infrastructure assets. This is achieved through an “all hazards” risk approach, requiring entities to capture and consider risks across four key domains of personnel, cyber, physical and supply chain related issues.
How does the SOCI Act impact cybersecurity practices for critical infrastructure?
SOCI introduces positive enhanced cyber security obligations on responsible entities. Importantly, this includes the requirement to report cyber security incidents and where business critical data is processed or stored by a third party on a commercial basis, take reasonable steps to inform the third party that they are doing so.
Where an asset has been identified as a SONS, additional cyber security obligations will be required under Part 2C of the SOCI Act.
Who does the SOCI Act apply to?
The SOCI Act covers 11 national critical infrastructures which includes communications, financial services and markets, data storage or processing, defence industry, higher education and research, energy, food and grocery, healthcare and medical, space technology, transport, water and sewerage.
What is a system of national significance?
A system of national significance (SONS) may be declared by the Minister who will notify the responsible entity in writing. In determining whether an asset is a SONS the Minister will give consideration to the impact on Australia’s national security, defence, or the social and economic stability of the country or our people should an asset be impacted.
The Minister may also identify an asset as a SONS where they become aware of interdependencies.
If your asset(s) are declared to be a SONS you will have increased obligations under the SOCI Act.
What are the main compliance requirements under the SOCI Act?
Requirements vary dependent on industry and asset criticality, however generally speaking they fall under the following areas:
Positive Security Obligations (PSO) – Mandates risk management programs, cyber incident reporting, and critical asset registration.
Enhanced Cyber Security Obligations (ECSO) – Applies to systems of national significance, requiring ongoing threat monitoring, vulnerability assessments, and incident response planning.
Government Assistance – Grants intervention powers for the government to respond to serious cyber threats impacting national security.
Compliance with these measures is essential to mitigating risks and ensuring resilience.
Development of a CIRMP
The CIRMP establishes the framework for how the entity will manage the risks related to their CI assets across the four SOCI domains. The CIRMP should be aligned and integrated into an entities established risk and resilience practices.
Where can I find official guidelines and resources on SOCI compliance?
For more guidance and up-to-date information:
Visit https://www.cisc.gov.au/legislation-regulation-and-compliance/soci-act-2018
Security of Critical Infrastructure Act 2018 General Guidance for Critical Infrastructure Assets
Contact us
Speak with a Thales Cyber Services ANZ
Security Specialist
Thales Cyber Services ANZ is a full-service cybersecurity and secure cloud services provider, partnering with clients from all industries and all levels of government. Let’s talk.

