Workforce Identity and Access Management (WIAM)
WIdentity and Access Management (IAM) controls keep your systems and data safe, no matter where your people are working from.

WIdentity and Access Management (IAM) controls keep your systems and data safe, no matter where your people are working from.
Thales Cyber Services ANZ is your partner in Identity and Access Management solutions: verifying users are truly who they say they are, and they’re allowed resource access. We offer expert help in modern workforce IAM to guard against fraudulent or unauthorised access, as a core pillar of your cybersecurity.
No matter your current IAM systems and setup, we’re here to help you with practical, seamless, trusted, compliant solutions that deliver value to your CISO and your users.
Identify gaps in identity and access strategies and systems
Create or refine federated digital identity services and controls
Identify, authenticate, and authorise users with confidence and compliance
De-risk your organisational architecture and data
Scale and grow your digital landscape securely with always-on IAM
Ours is a four-phase process:
IAM Review
IAM Strategy and Architecture
IAM Implementation and Uplift
IAM Managed Services
Workforce Identity and Access Management (IAM) is how we provision, control, and manage identity and access across an organisation’s diverse digital environment. From in-house networked teams to remote contractors on mobile BYOD, and on-site servers to public cloud resources, IAM ensures the right people have access to the right resources at the right time.
Drastically reduce the risk of data theft, leaks, and accidental deletion
Implement least privilege for tighter control
Ensure compliance with regulations such as NIST CSF and the Essential Eight
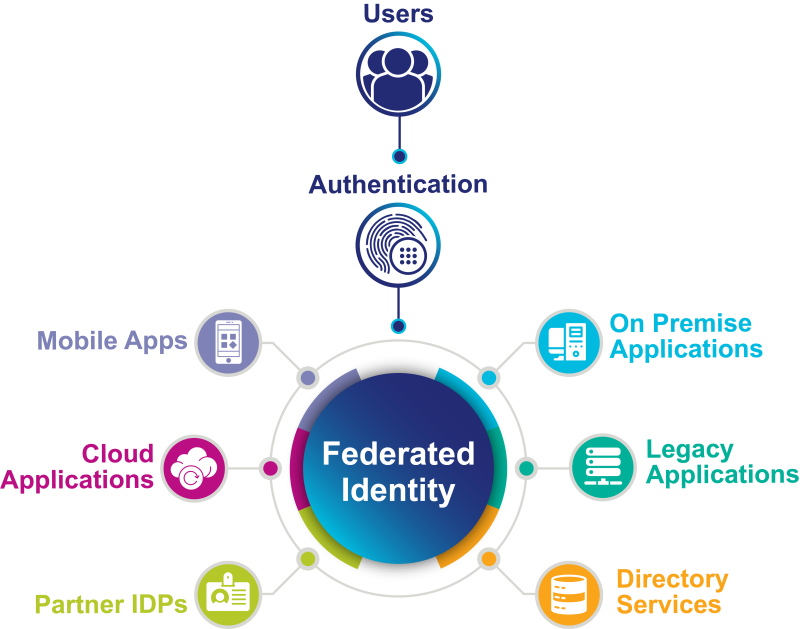
Offer a better user experience with Federated Identity across devices, systems, networks, platforms, and applications
Reduce customer support tickets and enquiries
Gain efficiencies in onboarding and offboarding users
Make application onboarding easier
Scale, so its complexity doesn’t increase under load
A thorough IAM Review will accurately gauge the current state and maturity of your IAM policies, procedures, and technologies – and where gaps lie.
Our IAM Review includes:
Authentication methodology review
Assessment of current IAM controls
IAM lifecycle review (onboarding, offboarding, role switching)
Role-based access control (RBAC) review
Privileged access management (PAM) review
The reporting phase will include gap analysis and risk overview which informs strategy.
An IAM Strategy and Architecture will identify organisational requirements, assets, users, and use cases, to inform an identity architecture, channels, technologies, controls, policies and processes.
We work with your current IAM solutions including Microsoft, SailPoint, Ping, Okta, OneWelcome by Thales, CyberArk, and more, to deliver real value on investment.
During IAM Implementation and Uplift, we build out to your custom IAM Strategy and Architecture. We assist in a broad range of tasks tailored to the environment, such as IT architecture, data migration, controls roll-out, optimising licensing, new IAM pilot programs, systems integration, cloud configuration, and user segmentation.
Identity and Access Management is a core component of many cybersecurity frameworks and legislations. We can assess and uplift your IAM to meet the NIST CSF, ISM, PSPF, ISO/IEC 24760, Essential Eight, KYC, and more.
With our IAM Managed Services, gain access to customer service for IAM, user lifecycle management, scheduled or on-demand RBAC and PAM reviews, and more. Choose our IAM Managed Services to remove administrative overheads.
Thales Cyber Services ANZ is a worldwide leader in Identity and Access Management, with over 110 identity specialists and deep experience with a wide range of organisations. Our IAM services are designed specifically for your needs and may include:
IAM Review
IAM Strategy and Architecture
IAM Implementation and Uplift
IAM Managed Services
Identity is a core element of every organisation’s cybersecurity. Ensure your IAM is protecting your organisation and people like it’s supposed to, with Thales Cyber Services ANZ.
Thales Cyber Services ANZ is a full-service cybersecurity and secure cloud services provider, partnering with clients from all industries and all levels of government. Let’s talk.