Posted by
Share this article
The International Society of Automation (ISA), in conjunction with the International Electrotechnical Commission (IEC), established a series of international standards for cybersecurity in Industrial Automation and Control Systems (IACS), known as ISA/IEC 62443.
The ISA/IEC 62443 standards for IACS provide a cybersecurity controls framework to guide organisations in ensuring adequate protection of complex Operational Technology (OT) environments while maintaining safety and reliability. These standards can be applied across industries regardless of their risk posture, compliance obligations, and OT assets within the environment.
While several cyber security standards exist, they were mainly developed to address cyber threats within Information Technology (IT) environments, focusing on data protection, financial impact, and availability of applications supporting business processes. For Operational Technology (OT) environments, in addition to the above, cyber risk expands to Health, Safety and Environment (HSE) factors and risks to assets of critical importance to national security.
The ISA/IEC 62443 series of standards were developed to support these unique requirements and provide a framework approach different from managing traditional IT cyber risks.
Introducing the IEC 62443 family
As established above, the IEC 62443 family of standards are designed to manage cyber risks across Operational Technology (OT) and Industrial Automation and Control Systems (IACS). They focus on cybersecurity controls across the manufacturing, deployment, integration, maintenance, and operation of IACS by defining policies, processes, procedures, and controls across people, processes, and technology.
IEC 62443 and modern OT environments
OT and IACS environments are traditionally physically separated from Enterprise/business networks and operations; any compromise to the environment or assets will require physical intervention. However, with technological advancement and requirements for business efficiencies, the last decade has seen an increase in the integration of OT assets with the broader enterprise network, expanding the cyber threat landscape.
The modern OT environment is interconnected, and remote access to OT sites is the new norm.
The IEC 63443 standards were designed to address the expanding threat landscape and should be highly considered as a mandatory framework for modern OT and IACS environments. The standard is developed to integrate into any existing cybersecurity framework/initiative and compliance obligations requirements and it covers:
- Requirements for establishing and operating an OT Security Program aligned to business objectives
- Guidance for determining security level requirements, ensuring commensurate measures are deployed across the OT environment, and providing effective resource allocation, including financial spending.
- Risk management methodologies appropriate to address OT risk, including Health, Safety and Environment (HSE) risks
- Processes for OT cybersecurity resiliency, including early incident detection and response and plans for effective incident recovery to minimise the impact on the business
- Strategies for continual improvement by defining measurement objectives across Security Program Maturity Levels and Technical Controls Security Level
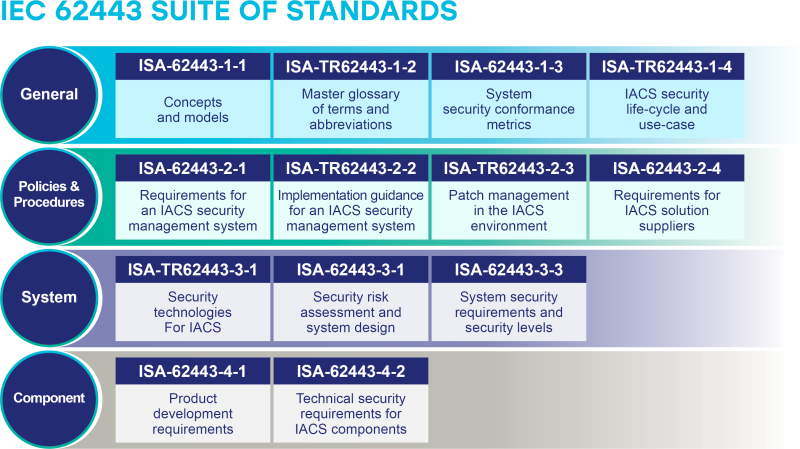
Structure of the ISA/IEC 62443 standards
Part 1 - General
- Part 1-1 Terminology, Concepts and Models
- Part 1-2 Master Glossary of Terms and Definitions
- Part 1-3 System Security Conformance Metrics
- Part 1-4 IACS Security Lifecycle Use Cases
Part 2 - Policies and Procedures
- Part 2-1 Establishing an Industrial Automation and Control System Security Program
- Part 2-2 IACS Security Program Ratings
- Part 2-3 Patch Management in the IACS Environment
- Part 2-4 Security Program Requirements for IACS Service Providers
- Part 2-5 Implementation Guidance for IACS Asset Owners
Part 3 - System
- Part 3-1 Security Technologies for IACS
- Part 3-2 Security Risk Assessment for System Design
- Part 3-3 System Security Requirements and Security Levels
Part 4 - Component
- Part 4-1 Product Security Development Lifecycle Requirements
- Part 4-2 Technical Security Requirements for IACS Components
Who should use the IEC 62443 standards and why?
Industrial control environments are complex, and the overall operations require skill sets typically provided across several entities. With this in mind, the IEC 62443 standards define roles and responsibilities within the IACS environment and provide frameworks specific to the individual roles.
Asset Owners
Asset owners are entities accountable for and/or operating the Industrial Control environment. They are typically concerned with the operational output of IACS and outsource systems implementation, technical operations, and day-to-day operations to other entities.
Integration Service Provider
Integration Service Providers are entities that design, deploy, commission and validate operations of the systems within the IACS. After successful validation, these entities hand over site operations to site operations (which may be the asset owners or any entity assigned to this capacity) to operate the site and to Maintenance Service Providers to provide maintenance and support.
Maintenance Service Provider
Maintenance Service Providers are entities with maintenance capabilities across the IACS and are also tasked with decommissioning obsolete services.
Product Suppliers
Product Suppliers are independent of the IACS environment; they manufacture, develop and support systems and components used within the IACS. These include physical components such as sensors and physical control devices, software applications controlling the physical components, and network and host devices supporting the communications between the physical components.
The Benefits of IEC 62443 for Different Roles
- Asset Owners: Develop a framework to prescribe policies, procedures, and processes to support cybersecurity within the IACS operational capabilities. This includes mitigating business risks, establishing security requirements for vendors, and addressing and meeting compliance and legislative obligations.
- Service Providers (Integration SPs and Maintenance SPs): Address technical and operational requirements to meet the criteria prescribed by the Asset Owners (typically contractual binding requirements). Integrate cyber resiliency in their operations to support IACS availability and business continuity, ensuring risk and hazards from cyber incidents are mitigated. Service providers integrating the IEC 62443 standards into their operations have a competitive advantage during asset owners' supplier selection processes.
- Product Suppliers: Design and produce IACS components to an international standard, outlining security requirements, achieving product security features, and providing product security updates. Aligning to the IEC 62443 standards, product suppliers showcase their commitment to cybersecurity and services as a competitive advantage during product selection for procurement.
IEC 62443 Certification
ISASecure, a part of the ISA Security Compliance Institute (ICSI), officiates certification to IEC 62443 standards. These certifications are aimed at Product Suppliers and Service Providers, providing recognition of their commitment to IACS security.. Organisations can certify the following:
- 62443-4-2 Component Security Assurance (CSA)
- 62443-4-2 IIoT Component Security Assurance (ICSA - IIOT)
- 62443-3-3 System Security Assurance (SSA)
- 62443-4-1 Security Development Lifecycle Assurance (SDLA)
Thales Cyber Services ANZ’s Solution for IEC 62443 Compliance
Thales Cyber Services ANZ helps IACS and OT asset owners, producers, and service providers comply with IEC 62443, with experience in assisting organisations in meeting the standards.
We listen first to the unique organisation's requirements and design a cybersecurity solution based on the appropriate sub-standards within the IEC 62443 suite of standards that address those needs and meet the business objectives.
Our specialties include:
- Establishing an IACS Security Program (2-1)
- Security Risk Assessments for System Design (3-2)
- System Security Requirements and Security Levels (3-3)
Our IEC 62443 offerings can be fused with complementary OT products and services for the Thales Cyber Services ANZ managed approach to OT cybersecurity.
Contact us
Speak with a Thales Cyber Services ANZ
Security Specialist
Thales Cyber Services ANZ is a full-service cybersecurity and secure cloud services provider, partnering with clients from all industries and all levels of government. Let’s talk.




