Posted by
Share this article
Third-Party Risk Management (TPRM) is risk management, tailored specifically for dealing with your organisation’s third parties. In relationships with third-party goods and service providers, there are often touchpoints where sensitive data is exchanged, which can leave your organisation open to security threats. Effectively assessing third parties as a whole and their service agreements as an extension of your own business practices, offers more comprehensive cybersecurity.
What is a Third-Party?
In the context of cyber risk, a third party is an entity that supplies physical or digital goods or services to your organisation. Typical third parties to an organisation include preferred vendors and contracted service providers. Examples of third parties include your business lawyer, externa marketing team, an IT service provider, a cloud storage vendor, a software provider whose SaaS you use to do business, essentially anything that is used to conduct your business.
What is a Fourth Party?
There are even fourth and fifth parties, which are your third party’s suppliers and their suppliers – culminating in what’s known as the supply chain. It can be nearly impossible to evaluate risk in your fourth and fifth parties, as third-party disclosure may be tricky. In very high security instances, however, investigation is warranted. In most cases it’s enough know and recognise that fourth and fifth parties – as well as other parties further down the line – can introduce risk into your operations.
Why is Third-Party Risk Management Important?
Understanding the cyber risk inherent in your third parties and their services is important to avoid negative consequences for your own business.
Let’s take the case of Ticketek Australia, who in May 2024 reported a customer data theft incident related to data stored on a third-party cloud platform. The data has since been offered up for sale on the dark web; the cause of this cyber incident is still unreported. The Ticketek incident is important because of its everyday innocuousness. Trusting a well-regarded third party with your customer’s data can still result in a notifiable and damaging data theft or breach, either due to errors in your own misconfiguration or on the part of the third party’s cyber security. These can result in fines and sanctions to your organisation; regardless of where the fault lies it is ultimately your customers’ data.
With each additional third party, and each additional third-party service, your organisation experiences a widening attack surface. What you need to ask yourself is whether that business and service meets your standards of cybersecurity.
Third parties and their services should be evaluated for cyber risk before entering into a business arrangement. For instance, when evaluating cloud storage providers, you might check whether your data is encrypted at rest by default.
Third party risk management is important in:
- Documenting the risks involved in third party relationships
- Evaluating vendors to ensure cybersecurity and compliance obligations are met
- Effectively reducing the risk of third-party cyber incidents
- Confidence in overall determinations of risk within the business
Common Third-Party Cyber Incidents
The same types of cyber incidents can occur at third parties that can occur within your own organisation. How these incidents affect downstream clients, like you, is another story. Here are some common third party cyber incidents and how they manage to trickle down the supply chain.
Data breaches
Sharing or storing your organisation’s sensitive data or Personally Identifying Information with third parties introduces the threat of data breach or theft.
Social engineering
When third parties are contracted to do work for the business, without internal cyber awareness training, these contractors can fall victim to obvious scams resulting in data leaks, financial fraud, or other negative consequences to your business.
Malware
Infected third-party systems or files have the potential to infect your own systems or cause disruption to your services, depending on the level of interconnection between your systems.
DDoS
Distributed Denial of Service attacks on a third party who you rely on for critical services can make a significant financial impact on your own business, thanks to the downtime associated with these attacks.
Effects of Third-Party Cyber Incidents
The effects of third party cyber incidents can be the same as a direct cyber incident within your business. Here are some typical negative business impacts resulting from third party cyber incidents.
Notifiable data breaches
Notifiable data breaches must be registered with the local responsible reporting body, such as the Office of the Australian Information Commissioner, and affected parties notified in a reasonable amount of time.
Legal fines and sanctions
Depending on the severity and legality of the third-party cyber incident, your organisation is at risk of large fines and business sanctions.
Operational losses
Third party incidents can affect your operations, resulting in lost profits, failure to meet service levels agreements, customer attrition, and more.
Compliance strikes
If the third party incident breaks a compliance obligation, your organisation is at risk of receiving a strike or penalty from the overseeing body.
Reputational damage
Depending on the effects on customers and whether a cyber incident is highly reported or circulated, your organisation can suffer from reputational damage.
What Are the Goals of Third-Party Risk Management?
The goals of Third-Party Risk Management (TPRM) include:
- Meeting compliance and legal obligations
- Meeting organisational standards of practice
- Avoiding predictable cyber incidents
- Determining appropriate risk treatments for third party relationships
- Ensuring the vendor supply chain is of a high quality
- Focusing on business continuity and performance goals
- Making sure third parties are scrutinised to meet the risk appetite of the business
What Are the Treatments for Third Party Risk?
Third party risks can be accepted, mitigated, avoided, transferred, or monitored, just like how you treat other forms of business risk.
Acceptance
The risk is accepted as is, with no vendor or internal accommodations necessary.
Mitigation
The risk is mitigated by extra provisions on the side of the vendor, within the organisation, or both.
Transference
The risk is transferred, by contractual financial obligations, insurance, or otherwise.
Avoidance
The risk is deemed unacceptable and other treatments not appropriate, thus the relationship is terminated.
Incident Planning
The risk is accepted, but deemed likely enough to warrant incident planning, to minimise the impact of an incident if and when it occurs.
Diversification
The risk is accepted, but redundancies are built in to ensure continuous business operations in the event of an incident.
What is a Third Party Risk Assessment?
A third party risk assessment is the review and scoring of a proposed or existing third party relationship to determine and document the risks to business. The third party risk assessment typically includes the third party itself as well as the product or service of investigation.
A risk assessment will determine the risks involved within the engagement, the severity of the risks (e.g. high or low impact), and how likely the risk is to eventuate. This risk assessment can them be used in combination with the organisation’s risk appetite statement, policy and procedures to determine the best course of action and appropriate risk treatment.
What Does a Third-Party Risk Management Program Look Like?
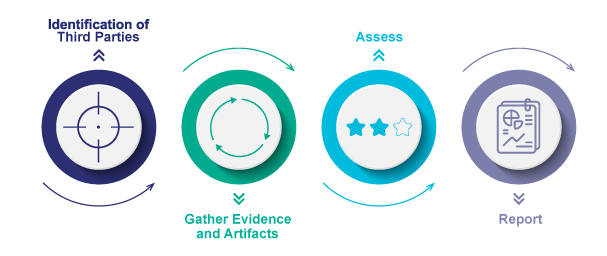
A TPRM program alleviates risks from third parties in a managed, repeatable process. The phases involved in TPRM include:
Review of current TPRM program
A thorough review of current TPRM policies, documentation, and risk assessment and treatment practices. This may include leveraging the ISO 31000 risk management framework.
Identification of third parties
Examine the breadth of third parties and their touchpoints within the organisation. For new vendors, complete initial due diligence by taking into account vendor security ratings or industry reputation.
Gather evidence and artifacts
Ask the vendor for further clarification and evidence of their security measures where necessary.
Assessment and reporting
In line with internal agreed upon risk grading policies, vendors and their products or services are assessed and a report drawn up for risk treatment.
Risk treatment
Depending on the outcome of the risk assessment and reporting, a vendor solution can be onboarded, rejected, or new guardrails put in place.
Continuous monitoring
Third parties and their solutions should be continuously monitored for risk, or at the least be placed under a periodic reassessment cycle.
TPRM Best Practices
Deploy best practices in third party risk management to ensure tight cyber security among your wide range of working relationships and products.
Develop policies and procedures for third party engagements that cover cyber security
When vendors use sensitive information or perform critical business functions, they need to be considered as an extended arm of the organisation. Developing policies and procedures for cybersecurity in third party engagements, which must be agreed to and tested, will ensure vendors meet your security terms.
Update risk management policies and procedures regularly
As time goes by, risk scenarios and the threat landscape change. This is particularly true as your business changes and evolves. Risk management policies and procedures should be regularly updated, as well as updated in the case of any major internal or external changes,
Document third parties and their associated risks
Third parties and their associated risks should be documented at all times in an up to date, historical, third-party risk register. The current risk management framework can be modified or addended to cover third party risk management.
Reassess third parties when relationships change
Third party relationships can become more entwined with your own business and assets, or less entwined. When third party relationships change in nature, you should conduct a new risk assessment to determine the new situation.
Ensure thorough offboarding when third party relationships end
Leaving third party relationships dangling and open when mutual operations have ended can result in unnecessary risk. Conducting process-bound offboarding can remove that risk.
Train departments and procurement in TPRM
Stakeholders in third party procurement and management must be trained in the risk management process so they are able to screen and manage vendors according to codified practices.
Continuous monitoring
Third parties should be monitored according to their risk level, either continuously, or with scheduled reassessments for lower-risk parties.
What Is a TPRM Assessment?
A TPRM assessment, or Third Party Risk Management assessment, assesses your internal policies, procedures, and practices in TPRM. By having an external assessor, such as Thales Cyber Services ANZ, come in and evaluate your current setup, you will:
- Ascertain the maturity of your current TPRM program
- Find any pitfalls in your current TPRM practices
- Discover new efficiencies in organisational TPRM
- Learn of new and emerging risks in third parties
How Thales Cyber Services ANZ Helps with Third Party Risk Management
Thales Cyber Services ANZ has years of experience in delivering Third Party Risk Management assessment and remediation services, built on a bank of expert knowledge and honed processes. We come ready with the latest best practices in discovery, assessment, prioritisation, remediation management, and continuous monitoring to ensure your organisation is always current-risk-aware moving forward.
Our tailored TPRM services include:
- TPRM Assessment
- TPRM Mitigation Strategy and Incident Response Development
- TPRM Remediation Services
- TPRM Ongoing Management Services
Written by Mark Jones
Contact us
Speak with a Thales Cyber Services ANZ
Security Specialist
Thales Cyber Services ANZ is a full-service cybersecurity and secure cloud services provider, partnering with clients from all industries and all levels of government. Let’s talk.