Posted by
Share this article
In his role as Senior Systems Engineer, Terry Lynch has been focused on using the full suite of Office 365 and Azure tools to improve productivity and collaboration within iQ3 while maintaining security of online services. Having a deep understanding of how modern teamwork looks allows us to better advise and work with our customers on solutions with these products.
In one recent project, Azure Multi-Factor authentication was enabled with Azure AD Identity Protection to help thwart suspicious logins and protect our information from leaked credentials. In this post we’ll explain why, how and general password guidelines for managing your users identities.
Passwords are no Longer Enough
With Azure AD accounts being available online, anyone with a username and password can log in and access all information which you have permissions to view. Phishing attacks, social engineering, credential leaks and brute-force guessing means that passwords are regularly compromised and cannot be trusted as the only method of securing an account from impersonation.
Azure AD has some safeguards in place to protect accounts and confirm that you (and only you) can log in with your credentials. These systems rely on monitoring and Artificial Intelligence to assign each logon request a “trust score” based on your location, device, if your credentials are leaked or if you are on an untrusted network. Depending on the trust score of your logon you will either be allowed in with just your password or your logon will be challenged with a Multi-Factor request.
What is Multi-Factor Authentication (MFA)?
Security systems generally rely on 4 different token types for access.
- Something you know (password)
- Something you have (RSA Token, Mobile Phone, etc.)
- Something you are (Biometrics, FaceID, Fingerprint scan, etc.)
- Somewhere you are (Geolocation, IP address)
A Multi-Factor request will require more than one of these tokens to grant access to systems. Most people are familiar with this from using online banking and resetting passwords for social and other network accounts.
Azure AD Identity Protection in practice
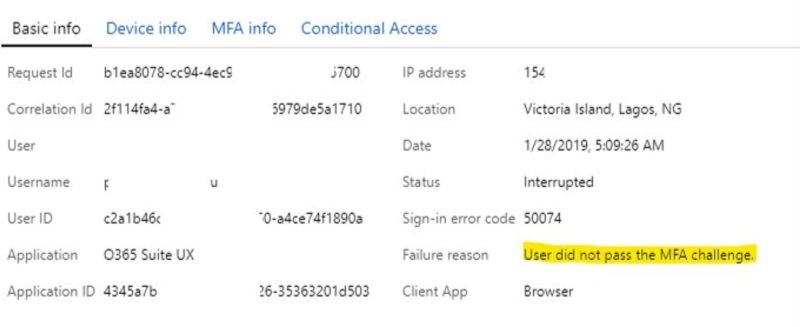
Several weeks after implementing these protections we were already benefiting from them when we received an alert that a member of staff had attempted login from an untrusted location but had failed to respond to their multi-factor prompt.
Instead of this being a major security breach we simply needed the staff member to change their password using Azure AD Self-Service Password Reset.
General Password Security
Multi-Factor is a great way to secure your accounts and you should enable it on any service that supports it. You should also follow these basic guidelines to ensure passwords remain secure and access is only granted to yourself.
Never tell anyone your password
The point of a username and password is to identify you as the person logging on. If someone needs access to a document or website they should have their own login and credentials.
Never write down or put your password near your desk
Post-it notes under the keyboard with passwords written on them are more common than you would expect. Passwords that are written down are accessible by anyone who can find them.
Always use long and complicated passwords
There are many methods to create complex passwords but generally, a longer password will be more secure than a short and complicated one.
Never Reuse Credentials across Sites
Websites are being hacked and credentials are being leaked every week. Companies like Adobe, MySpace and LinkedIn have all had breaches over the last few years where username/password combinations become publicly known. Attackers will immediately use these known combinations to try and log in to other services as password reuse is extremely common.
You can check if your email address has been a victim of public breach at Have I Been Pwned
To help with managing passwords, consider using a password manager such as LastPass, DashLane, 1Password or RoboForm
Contact us
Speak with a Thales Cyber Services ANZ
Security Specialist
Thales Cyber Services ANZ is a full-service cybersecurity and secure cloud services provider, partnering with clients from all industries and all levels of government. Let’s talk.




